update on 20221111
Startup with aws EC2
Login as ubuntu by
ssh -i "jean_aws_20190512.pem" ubuntu@18.203.160.207
sudo bash
apt update
apt dist-upgrade
root@ip-172-30-0-137:~# df -h Filesystem Size Used Avail Use% Mounted on udev 985M 0 985M 0% /dev tmpfs 200M 744K 199M 1% /run /dev/xvda1 24G 1.5G 22G 7% / tmpfs 996M 0 996M 0% /dev/shm tmpfs 5.0M 0 5.0M 0% /run/lock tmpfs 996M 0 996M 0% /sys/fs/cgroup /dev/loop0 91M 91M 0 100% /snap/core/6350 /dev/loop1 18M 18M 0 100% /snap/amazon-ssm-agent/930 tmpfs 200M 0 200M 0% /run/user/1000 root@ip-172-30-0-137:~#
#to avoid confusion put add future name at end of /etc/hostname:
root@ip-172-30-0-137:~# cat /etc/hostname ip-172-30-0-137-aws
Its imported to keep uid and guid similar to old/previous system.
Create new user
# adduser jean
# usermod -aG sudo jean
User jean can now transfer his old .ssh directory from neweraws.
Beware sudo will only work for user after system restart!!!
Packages unattended-upgrades is installed.
After the failed upgrade were /etc/lsb-release was upgraded but /etc/apt/sources.list was still on bionic the automatic update did not work. I got mails from apticron about a number of pacakages which could be upgraded BUT no upgrade was done.
root@ip-172-30-0-137-aws:/etc/apt/apt.conf.d/test# cat /etc/apt/apt.conf.d/10periodic APT::Periodic::Update-Package-Lists "1"; //APT::Periodic::Download-Upgradeable-Packages "0"; APT::Periodic::Download-Upgradeable-Packages "1"; // clean after 14 days APT::Periodic::AutocleanInterval "14"; root@ip-172-30-0-137-aws:/etc/apt/apt.conf.d/test# cat /etc/apt/apt.conf.d/20auto-upgrades APT::Periodic::Update-Package-Lists "1"; APT::Periodic::Unattended-Upgrade "1";Trying to install:
root@ip-172-30-0-137-aws:/etc/apt/apt.conf.d/test# apt install apt-config-auto-update Reading package lists... Done Building dependency tree Reading state information... Done The following NEW packages will be installed: apt-config-auto-update 0 upgraded, 1 newly installed, 0 to remove and 18 not upgraded. Need to get 2,040 B of archives. After this operation, 15.4 kB of additional disk space will be used. Get:1 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu focal/universe amd64 apt-config-auto-update all 2.1 [2,040 B] Fetched 2,040 B in 0s (12.8 kB/s) Selecting previously unselected package apt-config-auto-update. (Reading database ... 101840 files and directories currently installed.) Preparing to unpack .../apt-config-auto-update_2.1_all.deb ... Unpacking apt-config-auto-update (2.1) ... dpkg: error processing archive /var/cache/apt/archives/apt-config-auto-update_2.1_all.deb (--unpack): trying to overwrite '/etc/apt/apt.conf.d/10periodic', which is also in package update-notifier-common 3.192.30 Errors were encountered while processing: /var/cache/apt/archives/apt-config-auto-update_2.1_all.deb E: Sub-process /usr/bin/dpkg returned an error code (1)Apt-config-auto-update contains:
/etc/apt/apt.conf.d/10periodic /etc/apt/apt.conf.d/15update-stamp /etc/apt/apt.conf.d/20archive /usr/share/doc/apt-config-auto-update/changelog.gz /usr/share/doc/apt-config-auto-update/copyrightDifference are minor:
root@ip-172-30-0-137-aws:~/apt-config-auto-update# cat /etc/apt/apt.conf.d/10periodic
APT::Periodic::Update-Package-Lists "1";
//APT::Periodic::Download-Upgradeable-Packages "0";
APT::Periodic::Download-Upgradeable-Packages "1";
// clean after 14 days
APT::Periodic::AutocleanInterval "14";
root@ip-172-30-0-137-aws:~/apt-config-auto-update# cat ./etc/apt/apt.conf.d/10periodic
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Download-Upgradeable-Packages "1";
APT::Periodic::AutocleanInterval "0";
root@ip-172-30-0-137-aws:~/apt-config-auto-update# cat /etc/apt/apt.conf.d/15update-stamp
APT::Update::Post-Invoke-Success {"touch /var/lib/apt/periodic/update-success-stamp 2>/dev/null || true";};
root@ip-172-30-0-137-aws:~/apt-config-auto-update# cat ./etc/apt/apt.conf.d/15update-stamp
APT::Update::Post-Invoke {"touch /var/lib/apt/periodic/update-success-stamp 2>/dev/null || true";};
root@ip-172-30-0-137-aws:~/apt-config-auto-update# cat /etc/apt/apt.conf.d/20archive
APT::Archives::MaxAge "30";
APT::Archives::MinAge "2";
APT::Archives::MaxSize "500";
root@ip-172-30-0-137-aws:~/apt-config-auto-update# cat ./etc/apt/apt.conf.d/20archive
APT::Periodic::MaxAge "30";
APT::Periodic::MinAge "2";
APT::Periodic::MaxSize "500";
Nothing was changed and apt-config-auto-update is not installedInstall
Config$ sudo apt install unattended-upgrades
[sudo] password for jean:
Reading package lists... Done
Building dependency tree
Reading state information... Done
unattended-upgrades is already the newest version (0.90).
0 upgraded, 0 newly installed, 0 to remove and 65 not upgraded.
root@ip-172-30-0-137:/etc/apt/apt.conf.d# diff 50unattended-upgrades ../ORG/50unattended-upgrades
14c14
< "${distro_id}:${distro_codename}-updates";
---
> // "${distro_id}:${distro_codename}-updates";
52c52
< Unattended-Upgrade::Mail "root";
---
> //Unattended-Upgrade::Mail "root";
root@ip-172-30-0-137:/etc/apt/apt.conf.d# diff 10periodic ../ORG/10periodic 2,5c2,3 < //APT::Periodic::Download-Upgradeable-Packages "0"; < APT::Periodic::Download-Upgradeable-Packages "1"; < // clean after 14 days < APT::Periodic::AutocleanInterval "14"; --- > APT::Periodic::Download-Upgradeable-Packages "0"; > APT::Periodic::AutocleanInterval "0";
#root@ip-172-30-0-137:/etc/apt/apt.conf.d# cat /etc/apt/sources.list | egrep -v '^#' deb http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic main restricted deb-src http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic main restricted deb http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-updates main restricted deb-src http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-updates main restricted deb http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic universe deb-src http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic universe deb http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-updates universe deb-src http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-updates universe deb http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic multiverse deb-src http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic multiverse deb http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-updates multiverse deb-src http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-updates multiverse deb http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-backports main restricted universe multiverse deb-src http://eu-west-1.ec2.archive.ubuntu.com/ubuntu/ bionic-backports main restricted universe multiverse deb http://security.ubuntu.com/ubuntu bionic-security main restricted deb-src http://security.ubuntu.com/ubuntu bionic-security main restricted deb http://security.ubuntu.com/ubuntu bionic-security universe deb-src http://security.ubuntu.com/ubuntu bionic-security universe deb http://security.ubuntu.com/ubuntu bionic-security multiverse deb-src http://security.ubuntu.com/ubuntu bionic-security multiverse
# sudo apt install apticron
...
# vi /etc/apticron/apticron.conf
EMAIL="jean"
DNS aws.huens.be 34.252.180.134 (ip # of running aws instance)
apt install postfix
options internet site
mail_name aws.huens.be
root@ip-172-30-0-137-aws:~# cat /etc/aliases # See man 5 aliases for format postmaster: root root: jean, xtof
Mailutilsroot@ip-172-30-0-137-aws:~# apt install mailutils
root@ip-172-30-0-137-aws:/etc/postfix# cat main.cf
# See /usr/share/postfix/main.cf.dist for a commented, more complete version
# Debian specific: Specifying a file name will cause the first
# line of that file to be used as the name. The Debian default
# is /etc/mailname.
#myorigin = /etc/mailname
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
readme_directory = no
# See http://www.postfix.org/COMPATIBILITY_README.html -- default to 2 on
# fresh installs.
compatibility_level = 2
# TLS parameters
smtpd_tls_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
smtpd_tls_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
smtpd_use_tls=yes
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
# See /usr/share/doc/postfix/TLS_README.gz in the postfix-doc package for
# information on enabling SSL in the smtp client.
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
myhostname = aws.huens.be
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = $myhostname, aws.huens.be, ip-172-30-0-137-aws, localhost.localdomain, localhost
relayhost =
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
mailbox_size_limit = 0
recipient_delimiter = +
inet_interfaces = all
inet_protocols = all
mydomain = aws.huens.be
root@ip-172-30-0-137-aws:/etc/postfix#
And it receives mail over port 25:
jean@ip-172-30-0-100-neweraws:~$ telnet aws.huens.be 25
Trying 34.252.180.134...
Connected to aws.huens.be.
Escape character is '^]'.
220 aws.huens.be ESMTP Postfix (Ubuntu)
helo neweraws,huens.be
250 aws.huens.be
Mail from: <jean@huens.be>
250 2.1.0 Ok
RCPT to: <jean@aws.huens.be>
250 2.1.5 Ok
data
354 End data with <CR><LF>.<CR><LF>
from: <jean@huens.be>
to: <jean@aws.huens.be>
subject: test from neweraws
hallo
.
250 2.0.0 Ok: queued as 98D491395A6
quit
221 2.0.0 Bye
Connection closed by foreign host.
But it will not relay e-mail:
jean@ip-172-30-0-100-neweraws:~$ telnet aws.huens.be 25
Trying 34.252.180.134...
Connected to aws.huens.be.
Escape character is '^]'.
220 aws.huens.be ESMTP Postfix (Ubuntu)
helo neweraws,huens.be
250 aws.huens.be
Mail from: <jean.huens@gmail.com>
250 2.1.0 Ok
RCPT to: <rita.indeherberge@gmail.com>
454 4.7.1 <rita.indeherberge@gmail.com>: Relay access denied
RCPT to: <rita@huens.be>
454 4.7.1 <rita@huens.be>: Relay access denied
quit
221 2.0.0 Bye
Connection closed by foreign host.
Beware use postconf to edit mail.cf and other postfix config files!
To switch from mailboxes in /var/spool/mail to ~/MailDir:
# postconf -e 'home_mailbox = Maildir/'
You may need to change environment if you use e.g. mail or mailx:
export MAIL=~/Maildir
To let postfix use the SASL authentication (with dovecot login) :
postconf -e 'smtpd_sasl_auth_enable= yes'
postconf -e 'smtpd_sasl_path = private/auth'
postconf -e 'smtpd_sasl_type = dovecot'
postconf -e 'smtpd_client_restrictions = permit_sasl_authenticated'|
# previous line to permit user from
The last line is needed to prevent:
<jean@huens.be>: host vmailrelay3.cs.kuleuven.be[134.58.40.26] said: 553 5.1.8 <jean@huens.be>... Domain of sender address jean@aws.huens.be does not exist (in reply to RCPT TO command)
But this may be a temporary problem since aws.huens.be is frequently redefined in DNS ?
And reconfig dovecot
Thereafter authenthicated user can send mail to domains for which postfix does not relay.
This is done after upgrade to ubuntu 20.04 and only for domain purpur.be which was not used
for email and free for exepriments.
Purpur.be will be handled completely on aws.purpur.be = 34.241.93.195.
As documentation we did follow : https://petermolnar.net/article/howto-spf-dkim-dmarc-postfix/
and https://www.linuxbabe.com/mail-server/setting-up-dkim-and-spf (this one seems best)
jean@emilia1:~$ dig purpur.be spf ... ;; ANSWER SECTION: purpur.be. 18847 IN SPF "v=spf1 ip4:52.16.59.195 ip4:34.241.93.195 mx:purpur.be. |
a:mailrelay.cs.kuleuven.be a:mailrelay2.cs.kuleuven.be a:mailrelay3.cs.kuleuven.be \
a:vmailrelay1.cs.kuleuven.be a:vmailrelay2.cs.kuleuven.be a:vmailrelay3.cs.kuleuven.be |
include:amazonses.com ~all"
# apt install opendkim opendkim-tools
# gpasswd -a postfix opendkim Adding user postfix to group opendkim
#
....
# diff /etc/opendkim.conf /etc/opendkim.conf.ORG 19d18 < Canonicalization relaxed/simple 22,26d20 < AutoRestart yes < AutoRestartRate 10/1M < Background yes < DNSTimeout 5 < SignatureAlgorithm rsa-sha256 87,96d80 < < # Map domains in From addresses to keys used to sign messages < KeyTable refile:/etc/opendkim/key.table < SigningTable refile:/etc/opendkim/signing.table < < # Hosts to ignore when verifying signatures < ExternalIgnoreList /etc/opendkim/trusted.hosts < < # A set of internal hosts whose mail should be signed < InternalHosts /etc/opendkim/trusted.hosts # mkdir /etc/opendkim /etc/opendkim/keys # chown -R opendkim:opendkim /etc/opendkim # chmod go-rw /etc/opendkim/keys
# cat /etc/opendkim/signing.table # dkim sign purpur.be *@purpur.be default._domainkey.purpur.be
# cat /etc/opendkim/key.table # for purpur.be default._domainkey.purpur.be purpur.be:default:/etc/opendkim/keys/purpur.be/default.private
# cat /etc/opendkim/trusted.hosts # what should we do on aws ? 127.0.0.1 localhost *.purpur.be
# mkdir /etc/opendkim/keys/purpur.be
finally generate the key:
# opendkim-genkey -b 2048 -d purpur.be -D /etc/opendkim/keys/purpur.be -s default -v opendkim-genkey: generating private key opendkim-genkey: private key written to default.private opendkim-genkey: extracting public key opendkim-genkey: DNS TXT record written to default.txt # chown opendkim:opendkim /etc/opendkim/keys/purpur.be/default.private root@ip-172-30-0-137-aws:/etc# ls -l /etc/opendkim/keys/purpur.be/ total 8 -rw------- 1 opendkim opendkim 1675 Jul 21 15:34 default.private -rw------- 1 root root 505 Jul 21 15:34 default.txt
The file default.txt is the dkim record for purpur.be in DNS and must be inserteed there.:
# cat /etc/opendkim/keys/purpur.be/default.txt default._domainkey IN TXT ( "v=DKIM1; h=sha256; k=rsa; " "p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAw1cROVVLzhrAO352cZo4M1TxtVf48gxmuJfTNNXuILsWcnyWyJKRx/kdw7jaduUmBR/NpEHdZ2NqS4Q8CiCrujYWzWpGD1Blcqs21eB0BZtHYwFTGJeL6eHs0s5UfNEnOiVAUOs6aXT4VP+B1ncoS8JTDGLhFmvFtSUy5l876cCd2a+yka7JUcckulkWsADjk5TCbkZLpuDy/L" "xXffigFjwAxIU4dzlxVb1/7mYSrNGzxUXgkbA+4MsBrYlzhDGcOyqeuj0kIQC8+hissYbCG2scpj/jX8ovEuEZOTxI++gkYF5w6WbD5bS7XD66lirdMcoJq9AkOw/FNQgZW6cmBwIDAQAB" ) ; ----- DKIM key default for purpur.beTest the key :
# opendkim-testkey -d purpur.be -s default -vvv opendkim-testkey: using default configfile /etc/opendkim.conf opendkim-testkey: checking key 'default._domainkey.purpur.be' opendkim-testkey: key not secure opendkim-testkey: key OKConnect postfix to dkim:
The line "key not secure is a warning because we donot use DNSSEC
# mkdir /var/spool/postfix/opendkim # chown opendkim:postfix /var/spool/postfix/opendkim /etc/opendkim.conf Must conation line :Add the key to the opendkim key.table and the domain to the signing table
Socket local:/var/spool/postfix/opendkim/opendkim.sock
# cat /etc/opendkim/key.table # for purpur.be # cat /etc/opendkim/signing.table # dkim sign purpur.be *@purpur.be default._domainkey.purpur.be default._domainkey.purpur.be purpur.be:default:/etc/opendkim/keys/purpur.be/default.private
# systemctl restart opendkim
# systemctl status opendkim
● opendkim.service - OpenDKIM DomainKeys Identified Mail (DKIM) Milter
Loaded: loaded (/lib/systemd/system/opendkim.service; enabled; vendor preset: enabled)
Active: active (running) since Tue 2020-09-22 14:47:35 UTC; 13s ago
Docs: man:opendkim(8)
man:opendkim.conf(5)
man:opendkim-genkey(8)
man:opendkim-genzone(8)
man:opendkim-testadsp(8)
man:opendkim-testkey
http://www.opendkim.org/docs.html
Process: 320350 ExecStart=/usr/sbin/opendkim -x /etc/opendkim.conf (code=exited, status=0/SUCCESS)
Main PID: 320366 (opendkim)
Tasks: 7 (limit: 2341)
Memory: 3.5M
CGroup: /system.slice/opendkim.service
├─320366 /usr/sbin/opendkim -x /etc/opendkim.conf
└─320367 /usr/sbin/opendkim -x /etc/opendkim.conf
Sep 22 14:47:35 ip-172-30-0-137-aws systemd[1]: opendkim.service: Succeeded.
Sep 22 14:47:35 ip-172-30-0-137-aws systemd[1]: Stopped OpenDKIM DomainKeys Identified Mail (DKIM) Milter.
Sep 22 14:47:35 ip-172-30-0-137-aws systemd[1]: Starting OpenDKIM DomainKeys Identified Mail (DKIM) Milter...
Sep 22 14:47:35 ip-172-30-0-137-aws systemd[1]: opendkim.service: Can't open PID file /run/opendkim/opendkim.>
Sep 22 14:47:35 ip-172-30-0-137-aws systemd[1]: Started OpenDKIM DomainKeys Identified Mail (DKIM) Milter.
Sep 22 14:47:35 ip-172-30-0-137-aws opendkim[320367]: OpenDKIM Filter v2.11.0 starting (args: -x /etc/opendki>
DMARC consist in adding a dmarc record in dns:
; ; DMARC ; ; this record has no effect on the receiving side but causes statistics to be sent ;testing_dmarc.purpur.be. TXT "v=DMARC1; p=none; pct=100; fo=1; rua=mailto:postmaster@purpur.be"Remote site receiving mail from us will now handle mails from @purpur,be following this DMARC record. (process the mail but generate a report if SPF or DKIM fail).
root@ip-172-30-0-137-aws:~# apt install opendmarc Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: dbconfig-common dbconfig-mysql default-mysql-client libdbd-mysql-perl libdbi-perl libopendbx1-mysql libopendmarc2 libspf2-2 libswitch-perl mysql-client-8.0 mysql-client-core-8.0 Suggested packages: default-mysql-server | virtual-mysql-server libclone-perl libmldbm-perl libnet-daemon-perl libsql-statement-perl python-mysqldb libxml-simple-perl The following NEW packages will be installed: dbconfig-common dbconfig-mysql default-mysql-client libdbd-mysql-perl libdbi-perl libopendbx1-mysql libopendmarc2 libspf2-2 libswitch-perl mysql-client-8.0 mysql-client-core-8.0 opendmarc 0 upgraded, 12 newly installed, 0 to remove and 0 not upgraded. Need to get 5,822 kB of archives. After this operation, 69.6 MB of additional disk space will be used. Do you want to continue? [Y/n] y
......
root@ip-172-30-0-137-aws:~# systemctl status opendmarc ● opendmarc.service - OpenDMARC Milter Loaded: loaded (/lib/systemd/system/opendmarc.service; enabled; vendor preset: enabled) Active: active (running) since Fri 2020-09-25 09:34:30 UTC; 2min 1s ago Docs: man:opendmarc(8) man:opendmarc.conf(5) Main PID: 54411 (opendmarc) Tasks: 6 (limit: 2341) Memory: 1.3M CGroup: /system.slice/opendmarc.service └─54411 /usr/sbin/opendmarc Sep 25 09:34:30 ip-172-30-0-137-aws systemd[1]: Starting OpenDMARC Milter... Sep 25 09:34:30 ip-172-30-0-137-aws systemd[1]: opendmarc.service: Can't open PID file /run/opendmarc/opendma> Sep 25 09:34:30 ip-172-30-0-137-aws opendmarc[54411]: OpenDMARC Filter v1.3.2 starting () Sep 25 09:34:30 ip-172-30-0-137-aws opendmarc[54411]: additional trusted authentication services: (none) Sep 25 09:34:30 ip-172-30-0-137-aws systemd[1]: Started OpenDMARC Milter. root@ip-172-30-0-137-aws:~# systemctl enable opendmarc
Change opendmarc configuration:
root@ip-172-30-0-137-aws:/etc# diff /etc/opendmarc.conf /etc/opendmarc.conf.ORG 14d13 < AuthservID OpenDMARC 54,55d52 < # RejectFailures true # not yet < RejectFailures false 70,72c67 < #Socket local:/var/run/opendmarc/opendmarc.sock < # postfix runs chrooted < Socket local:/var/spool/postfix/opendmarc/opendmarc.sock --- > Socket local:/var/run/opendmarc/opendmarc.sock 99,100d93 < # amavisd-new uses aws.huens.be , postfix myhostname is aws.huens.be, < TrustedAuthservIDs aws.huens.be 122,127d114 < # desktop/mobile mail clients that submit outgoing emails over port 587 ? < IgnoreAuthenticatedClients true < #reject emails that don’t conform to email header standards as described in RFC5322 < RequiredHeaders true < # This will make OpenDMARC perform a fallback SPF check itself when it can find no SPF results in the message header < SPFSelfValidate true
Integration with postfix
root@ip-172-30-0-137-aws:/# mkdir -p /var/spool/postfix/opendmarc root@ip-172-30-0-137-aws:/# chown opendmarc:opendmarc /var/spool/postfix/opendmarc -R root@ip-172-30-0-137-aws:/# chmod 750 /var/spool/postfix/opendmarc/ -R root@ip-172-30-0-137-aws:/# adduser postfix opendmarc Adding user `postfix' to group `opendmarc' ... Adding user postfix to group opendmarc Done.
root@ip-172-30-0-137-aws:/# diff /etc/postfix/main.cf /etc/postfix/main.cf.20200925 87c87 < smtpd_milters = local:opendkim/opendkim.sock,local:opendmarc/opendmarc.sock --- > smtpd_milters = local:opendkim/opendkim.sock root@ip-172-30-0-137-aws:/etc/postfix#
Install
jean@ip-172-30-0-137-aws:/etc/profile.d$ sudo apt install dovecot-imapd Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: liblockfile-bin liblockfile1 Use 'sudo apt autoremove' to remove them. The following additional packages will be installed: dovecot-core libexttextcat-2.0-0 libexttextcat-data Suggested packages: dovecot-gssapi dovecot-ldap dovecot-lmtpd dovecot-managesieved dovecot-mysql dovecot-pgsql dovecot-pop3d dovecot-sieve dovecot-solr dovecot-sqlite ntp The following NEW packages will be installed: dovecot-core dovecot-imapd libexttextcat-2.0-0 libexttextcat-data 0 upgraded, 4 newly installed, 0 to remove and 0 not upgraded. Need to get 3,067 kB of archives. After this operation, 9,765 kB of additional disk space will be used. Do you want to continue? [Y/n] y Get:1 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic/main amd64 libexttextcat-data all 3.4.5-1 [162 kB] Get:2 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic/main amd64 libexttextcat-2.0-0 amd64 3.4.5-1 [13.0 kB] Get:3 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic-updates/main amd64 dovecot-core amd64 1:2.2.33.2-1ubuntu4.3 [2,739 kB] Get:4 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic-updates/main amd64 dovecot-imapd amd64 1:2.2.33.2-1ubuntu4.3 [153 kB] Fetched 3,067 kB in 0s (22.6 MB/s) Selecting previously unselected package libexttextcat-data. (Reading database ... 113305 files and directories currently installed.) Preparing to unpack .../libexttextcat-data_3.4.5-1_all.deb ... Unpacking libexttextcat-data (3.4.5-1) ... Selecting previously unselected package libexttextcat-2.0-0:amd64. Preparing to unpack .../libexttextcat-2.0-0_3.4.5-1_amd64.deb ... Unpacking libexttextcat-2.0-0:amd64 (3.4.5-1) ... Selecting previously unselected package dovecot-core. Preparing to unpack .../dovecot-core_1%3a2.2.33.2-1ubuntu4.3_amd64.deb ... Unpacking dovecot-core (1:2.2.33.2-1ubuntu4.3) ... Selecting previously unselected package dovecot-imapd. Preparing to unpack .../dovecot-imapd_1%3a2.2.33.2-1ubuntu4.3_amd64.deb ... Unpacking dovecot-imapd (1:2.2.33.2-1ubuntu4.3) ... Processing triggers for ufw (0.36-0ubuntu0.18.04.1) ... Processing triggers for ureadahead (0.100.0-21) ... Processing triggers for libc-bin (2.27-3ubuntu1) ... Setting up libexttextcat-data (3.4.5-1) ... Processing triggers for systemd (237-3ubuntu10.21) ... Processing triggers for man-db (2.8.3-2ubuntu0.1) ... Setting up libexttextcat-2.0-0:amd64 (3.4.5-1) ... Setting up dovecot-core (1:2.2.33.2-1ubuntu4.3) ... Creating config file /etc/dovecot/dovecot.conf with new version Creating config file /etc/dovecot/dovecot-dict-auth.conf.ext with new version Creating config file /etc/dovecot/dovecot-dict-sql.conf.ext with new version Creating config file /etc/dovecot/dovecot-sql.conf.ext with new version Creating config file /etc/dovecot/conf.d/10-auth.conf with new version Creating config file /etc/dovecot/conf.d/10-director.conf with new version Creating config file /etc/dovecot/conf.d/10-logging.conf with new version Creating config file /etc/dovecot/conf.d/10-mail.conf with new version Creating config file /etc/dovecot/conf.d/10-master.conf with new version Creating config file /etc/dovecot/conf.d/10-ssl.conf with new version Creating config file /etc/dovecot/conf.d/10-tcpwrapper.conf with new version Creating config file /etc/dovecot/conf.d/15-lda.conf with new version Creating config file /etc/dovecot/conf.d/15-mailboxes.conf with new version Creating config file /etc/dovecot/conf.d/90-acl.conf with new version Creating config file /etc/dovecot/conf.d/90-plugin.conf with new version Creating config file /etc/dovecot/conf.d/90-quota.conf with new version Creating config file /etc/dovecot/conf.d/auth-checkpassword.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-deny.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-dict.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-master.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-passwdfile.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-sql.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-static.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-system.conf.ext with new version Creating config file /etc/dovecot/conf.d/auth-vpopmail.conf.ext with new version Created symlink /etc/systemd/system/multi-user.target.wants/dovecot.service → /lib/systemd/system/dovecot.service. Setting up dovecot-imapd (1:2.2.33.2-1ubuntu4.3) ... ...
root@ip-172-30-0-137-aws:/etc/profile.d# netstat -ntlp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:143 0.0.0.0:* LISTEN 13457/dovecot tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 634/systemd-resolve tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 939/sshd tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 9762/master tcp 0 0 0.0.0.0:993 0.0.0.0:* LISTEN 13457/dovecot tcp6 0 0 :::143 :::* LISTEN 13457/dovecot tcp6 0 0 :::22 :::* LISTEN 939/sshd tcp6 0 0 :::25 :::* LISTEN 9762/master tcp6 0 0 :::993 :::* LISTEN 13457/dovecot root@ip-172-30-0-137-aws:/etc/profile.d#
Dovecot /etc/dovecot/10
root@ip-172-30-0-137-aws:/etc/postfix# diff /etc/dovecot/conf.d/10-mail.conf /etc/dovecot/conf.d/10-mail.conf.ORG
30,31c30
< #mail_location = mbox:~/mail:INBOX=/var/mail/%u
< mail_location = maildir:~/Maildir
---
> mail_location = mbox:~/mail:INBOX=/var/mail/%u
Postfix on port 465
root@ip-172-30-0-137-aws:/etc/postfix# grep smtps master.cf #smtps inet n - y - - smtpd # -o syslog_name=postfix/smtps smtps inet n - y - - smtpd
Dovecot uses postfix
root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# diff 10-master.conf 10-master.conf.ORG
89,93c89,93
< ## unix_listener auth-userdb {
< ## #mode = 0666
< ## #user =
< ## #group =
< ## }
---
> unix_listener auth-userdb {
> #mode = 0666
> #user =
> #group =
> }
99,104d98
< unix_listener /var/spool/postfix/private/auth {
< mode = 0660
< # Assuming the default Postfix user and group
< user = postfix
< group = postfix
< }
root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# diff 10-auth.conf 10-auth.conf.ORG
100c100
< auth_mechanisms = plain login
---
> auth_mechanisms = plain
Next
o not do this:
Postfix changed after 2.10 but these instruction are outdated sincesmtpd_recipient_restrictions
is implemented by preference with
smtpd_relay_restrictions and its default is OK:
root@ip-172-30-0-137-aws:~# postconf smtpd_relay_restrictions
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
changed postfix params based on http://jimsun.linxnet.com/misc/postfix-anti-UCE.txt :
root@ip-172-30-0-137-aws:/etc/postfix# diff main.cf main.cf.201905231550
53,54d52
< smtpd_recipient_restrictions = reject_invalid_hostname, reject_non_fqdn_hostname, reject_non_fqdn_sender, reject_non_fqdn_recipient, reject_unknown_sender_domain, reject_unknown_recipient_domain, permit_mynetworks, reject_unauth_destination,reject_rbl_client sbl.spamhaus.org,permit
< smtpd_data_restrictions = reject_unauth_pipelining,permit
next
install
oot@ip-172-30-0-137-aws:/etc/postfix# apt install clamav clamav-docs clamav-freshclam ibclamunrar7 clamav-daemon Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: liblockfile-bin liblockfile1 Use 'apt autoremove' to remove them. The following additional packages will be installed: clamav-base libclamav7 libllvm3.9 libtfm1Next instructions install clamsmtp, but we donot use it since it conflicts with amavis.
root@ip-172-30-0-137-aws:/etc/clamav# apt install clamsmtp
root@ip-172-30-0-137-aws:/etc/clamav# diff /etc/clamsmtpd.conf /etc/clamsmtpd.conf.ORG
11c11
< OutAddress: 10026
---
> OutAddress: 10025
21c21
< Listen: 127.0.0.1:10025
---
> Listen: 127.0.0.1:10026
root@ip-172-30-0-137-aws:/etc/clamav# systemctl restart clamsmtp
Adapt postfix:
root@ip-172-30-0-137-aws:/etc/clamav# postconf -e 'content_filter = scan:127.0.0.1:10025'
root@ip-172-30-0-137-aws:/etc/clamav# postconf -e 'receive_override_options = no_address_mappings'
vi /etc/postfix/master.cf
,,,
root@ip-172-30-0-137-aws:/etc/postfix# netstat -ntpl
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:10026 0.0.0.0:* LISTEN 5466/master
tcp 0 0 0.0.0.0:143 0.0.0.0:* LISTEN 2570/dovecot
tcp 0 0 0.0.0.0:465 0.0.0.0:* LISTEN 5466/master
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 636/systemd-resolve
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 970/sshd
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 5466/master
tcp 0 0 0.0.0.0:993 0.0.0.0:* LISTEN 2570/dovecot
tcp 0 0 127.0.0.1:10025 0.0.0.0:* LISTEN 5290/clamsmtpd
tcp6 0 0 :::143 :::* LISTEN 2570/dovecot
tcp6 0 0 :::465 :::* LISTEN 5466/master
tcp6 0 0 :::22 :::* LISTEN 970/sshd
tcp6 0 0 :::25 :::* LISTEN 5466/master
tcp6 0 0 :::993 :::* LISTEN 2570/dovecot
Test mail with smtp to port 25. The /var/log/syslog shows clamsmtp works.
End of clamsmtp installation
clamav-daemon starts clamd. It uses /etc/clamav/clamd.conf. If needed this file must be regenerated with:
# dpkg-reconfigure clamav-daemonLog file is /var/log/clamav/clamd.log
Postfix documentation points to https://www.ijs.si/
We did follow https://www.ijs.si/software/amavisd/README.postfix.html
Its probably better to use https://help.ubuntu.com/community/PostfixAmavisNew as install guide
(see below)
Install
root@ip-172-30-0-137-aws:~# apt install amavisd-new amavisd-milter Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: liblockfile-bin liblockfile1 Use 'apt autoremove' to remove them. The following additional packages will be installed: libarchive-zip-perl libauthen-sasl-perl libberkeleydb-perl libcgi-fast-perl libcgi-pm-perl libconvert-binhex-perl libconvert-tnef-perl libconvert-uulib-perl libcrypt-openssl-bignum-perl libcrypt-openssl-rsa-perl libdigest-hmac-perl libencode-locale-perl libfcgi-perl libhtml-parser-perl libhtml-tagset-perl libhttp-date-perl libhttp-message-perl libio-html-perl libio-multiplex-perl libio-socket-inet6-perl libio-socket-ssl-perl libio-stringy-perl liblwp-mediatypes-perl libmail-dkim-perl libmailtools-perl libmilter1.0.1 libmime-tools-perl libnet-cidr-lite-perl libnet-cidr-perl libnet-dns-perl libnet-ip-perl libnet-libidn-perl libnet-patricia-perl libnet-server-perl libnet-smtp-ssl-perl libnet-ssleay-perl libsocket6-perl libtimedate-perl libunix-syslog-perl liburi-perl pax perl-openssl-defaults Suggested packages: apt-listchanges arj cabextract dspam lhasa libdbi-perl libnet-ldap-perl libsnmp-perl libzeromq-perl lzop nomarch p7zip rpm spamassassin unrar altermime ripole libgssapi-perl libdata-dump-perl liblog-log4perl-perl libwww-perl The following NEW packages will be installed: amavisd-milter amavisd-new libarchive-zip-perl libauthen-sasl-perl libberkeleydb-perl libcgi-fast-perl libcgi-pm-perl libconvert-binhex-perl libconvert-tnef-perl libconvert-uulib-perl libcrypt-openssl-bignum-perl libcrypt-openssl-rsa-perl libdigest-hmac-perl libencode-locale-perl libfcgi-perl libhtml-parser-perl libhtml-tagset-perl libhttp-date-perl libhttp-message-perl libio-html-perl libio-multiplex-perl libio-socket-inet6-perl libio-socket-ssl-perl libio-stringy-perl liblwp-mediatypes-perl libmail-dkim-perl libmailtools-perl libmilter1.0.1 libmime-tools-perl libnet-cidr-lite-perl libnet-cidr-perl libnet-dns-perl libnet-ip-perl libnet-libidn-perl libnet-patricia-perl libnet-server-perl libnet-smtp-ssl-perl libnet-ssleay-perl libsocket6-perl libtimedate-perl libunix-syslog-perl liburi-perl pax perl-openssl-defaults 0 upgraded, 44 newly installed, 0 to remove and 0 not upgraded. ...
FAILS:
May 24 09:16:13 ip-172-30-0-137-aws systemd[1]: Starting LSB: Starts amavisd-new mailfilter... May 24 09:16:14 ip-172-30-0-137-aws amavis[3995]: Starting amavisd: The value of variable $myhostname is "ip-172-30-0-137-aws", but should have been May 24 09:16:14 ip-172-30-0-137-aws amavis[3995]: a fully qualified domain name; perhaps uname(3) did not provide such. May 24 09:16:14 ip-172-30-0-137-aws amavis[3995]: You must explicitly assign a FQDN of this host to variable $myhostname May 24 09:16:14 ip-172-30-0-137-aws amavis[3995]: in /etc/amavis/conf.d/05-node_id, or fix what uname(3) provides as a host's May 24 09:16:14 ip-172-30-0-137-aws amavis[3995]: network name! May 24 09:16:14 ip-172-30-0-137-aws amavis[3995]: (failed). ...
root@ip-172-30-0-137-aws:~# cat /etc/amavis/conf.d/05-node_id use strict; # $myhostname is used by amavisd-new for node identification, and it is # important to get it right (e.g. for ESMTP EHLO, loop detection, and so on). chomp($myhostname = `hostname --fqdn`); # To manually set $myhostname, edit the following line with the correct Fully # Qualified Domain Name (FQDN) and remove the # at the beginning of the line. # #$myhostname = "mail.example.com"; $myhostname = "aws.huens.be"; 1; # ensure a defined return root@ip-172-30-0-137-aws:~# systemctl restart amavisd-new
root@ip-172-30-0-137-aws:~# apt install amavisd-new-postfix
The following additional packages will be installed: binutils binutils-common binutils-x86-64-linux-gnu cpp cpp-7 gcc gcc-7 gcc-7-base libasan4 libatomic1 libbinutils libc-dev-bin libc6-dev libcc1-0 libcilkrts5 libgcc-7-dev libgomp1 libisl19 libitm1 liblsan0 libmail-spf-perl libmpc3 libmpx2 libnetaddr-ip-perl libquadmath0 libsys-hostname-long-perl libtsan0 libubsan0 linux-libc-dev make manpages-dev postfix-policyd-spf-python python3-authres python3-dns python3-spf re2c sa-compile spamassassin spamc unzip Suggested packages: binutils-doc cpp-doc gcc-7-locales gcc-multilib autoconf automake libtool flex bison gdb gcc-doc gcc-7-multilib gcc-7-doc libgcc1-dbg libgomp1-dbg libitm1-dbg libatomic1-dbg libasan4-dbg liblsan0-dbg libtsan0-dbg libubsan0-dbg libcilkrts5-dbg libmpx2-dbg libquadmath0-dbg glibc-doc make-doc razor libdbi-perl pyzor libencode-detect-perl libgeo-ip-perl zip Recommended packages: zoo unarj The following NEW packages will be installed: amavisd-new-postfix binutils binutils-common binutils-x86-64-linux-gnu cpp cpp-7 gcc gcc-7 gcc-7-base libasan4 libatomic1 libbinutils libc-dev-bin libc6-dev libcc1-0 libcilkrts5 libgcc-7-dev libgomp1 libisl19 libitm1 liblsan0 libmail-spf-perl libmpc3 libmpx2 libnetaddr-ip-perl libquadmath0 libsys-hostname-long-perl libtsan0 libubsan0 linux-libc-dev make manpages-dev postfix-policyd-spf-python python3-authres python3-dns python3-spf re2c sa-compile spamassassin spamc unzip 0 upgraded, 41 newly installed, 0 to remove and 0 not upgraded. Need to get 29.0 MB of archives. After this operation, 122 MB of additional disk space will be used. ....
Setting up amavisd-new-postfix (1:2.11.0-1ubuntu1.1) ... postconf: warning: policy-spf_time_limit: unknown parameter postconf: warning: /etc/postfix/main.cf: unused parameter: policy-spf_time_limit=3600s postconf: warning: /etc/postfix/main.cf: unused parameter: policy-spf_time_limit=3600s Setting up binutils (2.30-21ubuntu1~18.04.1) ... Setting up gcc-7 (7.4.0-1ubuntu1~18.04) ... Setting up gcc (4:7.4.0-1ubuntu2.2) ... Setting up sa-compile (3.4.2-0ubuntu0.18.04.1) ... Running sa-compile (may take a long time) Processing triggers for libc-bin (2.27-3ubuntu1) ... Processing triggers for ureadahead (0.100.0-21) ... Processing triggers for systemd (237-3ubuntu10.21) ... root@ip-172-30-0-137-aws:~#postconf -e "soft_bounce = yes"
With ubuntu guide (after steps above)
root@ip-172-30-0-137-aws:/etc/init.d# apt install amavisd-new spamassassin clamav-daemon
Reading package lists... Done
Building dependency tree
Reading state information... Done
amavisd-new is already the newest version (1:2.11.0-1ubuntu1.1).
clamav-daemon is already the newest version (0.100.3+dfsg-0ubuntu0.18.04.1).
spamassassin is already the newest version (3.4.2-0ubuntu0.18.04.1).
spamassassin set to manually installed.
The following packages were automatically installed and are no longer required:
liblockfile-bin liblockfile1
Use 'apt autoremove' to remove them.
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
root@ip-172-30-0-137-aws:/etc/init.d# apt install libnet-dns-perl libmail-spf-perl pyzor razor
Reading package lists... Done
Building dependency tree
Reading state information... Done
libmail-spf-perl is already the newest version (2.9.0-4).
libmail-spf-perl set to manually installed.
libnet-dns-perl is already the newest version (1.10-2).
libnet-dns-perl set to manually installed.
Suggested packages:
pyzor-doc
The following NEW packages will be installed:
pyzor razor
0 upgraded, 2 newly
root@ip-172-30-0-137-aws:/etc/init.d# apt install arj bzip2 cabextract cpio file gzip nomarch pax rar unrar unzip zip
Reading package lists... Done
Building dependency tree
Reading state information... Done
bzip2 is already the newest version (1.0.6-8.1).
cpio is already the newest version (2.12+dfsg-6).
gzip is already the newest version (1.6-5ubuntu1).
pax is already the newest version (1:20171021-2).
pax set to manually installed.
unzip is already the newest version (6.0-21ubuntu1).
unzip set to manually installed.
file is already the newest version (1:5.32-2ubuntu0.2).
The following NEW packages will be installed:
arj cabextract nomarch rar unrar zip
0 upgraded, 6 newly installed, 0 to remove and 0 not upgraded.
Need to get 847 kB of archives.
After this operation, 2,511 kB of additional disk space will be used.
installed, 0 to remove and 0 not upgraded.
Need to get 128 kB of archives.
...
root@ip-172-30-0-137-aws:/etc/init.d# adduser clamav amavis
Adding user `clamav' to group `amavis' ...
Adding user clamav to group amavis
Done.
root@ip-172-30-0-137-aws:/etc/init.d# adduser amavis clamav
Adding user `amavis' to group `clamav' ...
Adding user amavis to group clamav
Done.
root@ip-172-30-0-137-aws:/etc/clamav# apt --purge remove clamsmtp
Configure spamassassin; amavis will only use its libraries:
root@ip-172-30-0-137-aws:/etc/clamav# su - amavis -s /bin/bash
$ razor-admin -create
$ razor-admin -register
Register successful. Identity stored in /var/lib/amavis/.razor/identity-ruQhghua86
$ pyzor discover
2019-05-24 13:15:28,201 (12352) CRITICAL Unknown command: discover
$ logout
root@ip-172-30-0-137-aws:/etc/clamav#
amavis configuration:
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# diff ../ORG/15-content_filter_mode 15-content_filter_mode
13,14c13,14
< #@bypass_virus_checks_maps = (
< # \%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re);
---
> @bypass_virus_checks_maps = (
> \%bypass_virus_checks, \@bypass_virus_checks_acl, \$bypass_virus_checks_re);
24,25c24,25
< #@bypass_spam_checks_maps = (
< # \%bypass_spam_checks, \@bypass_spam_checks_acl, \$bypass_spam_checks_re);
---
> @bypass_spam_checks_maps = (
> \%bypass_spam_checks, \@bypass_spam_checks_acl, \$bypass_spam_checks_re);
Interation in postfix:
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# postconf content_filter
content_filter = smtp-amavis:[localhost]:10024
After restarting postfix, amavisd-new and clamav-daemon We can deliver mail to aws.huens.be
and it gets passed to amavis and clamav.
amavisd-milter is not needed and can be removed
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# apt --purge remove amavisd-milter
changes to amavis to mark dtecetd spam:
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# cat /etc/amavis/conf.d/50-user use strict; # # Place your configuration directives here. They will override those in # earlier files. # # See /usr/share/doc/amavisd-new/ for documentation and examples of # the directives you can use in this file # use strict; $sa_spam_subject_tag = '[SPAM] '; $sa_tag_level_deflt = 0.0; # add spam info headers if at, or above that level #$sa_tag_level_deflt = -999; # allways add spam info headers if at, or above that level $sa_tag2_level_deflt = 4.0; # add 'spam detected' headers at that level $sa_kill_level_deflt = 6.31; # triggers spam evasive actions $sa_dsn_cutoff_level = 10; # spam level beyond which a DSN is not sent $sa_mail_body_size_limit = 200*1024; # don't waste time on SA if mail is larger $sa_local_tests_only = 0; # only tests which do not require internet access? #------------ Do not modify anything below this line ------------- 1; # ensure a defined return
clamscan works but takes a lot ot fimr to start:
root@ip-172-30-0-137-aws:/home/jean# clamscan -i /home/jean/eicar/ /home/jean/eicar/eicar.com.txt: Win.Test.EICAR_HDB-1 FOUND /home/jean/eicar/eicar.com: Win.Test.EICAR_HDB-1 FOUND /home/jean/eicar/eicar_com.zip: Win.Test.EICAR_HDB-1 FOUND /home/jean/eicar/eicarcom2.zip: Win.Test.EICAR_HDB-1 FOUND ----------- SCAN SUMMARY ----------- Known viruses: 8243665 Engine version: 0.102.3 Scanned directories: 1 Scanned files: 4 Infected files: 4 Data scanned: 0.00 MB Data read: 0.00 MB (ratio 0.00:1) Time: 32.641 sec (0 m 32 s)
Outgoing mails containing eicar will be detected, refused and marked in syslog
Incoming mails via port 25 : test not delivered but why ?
On ubuntu 20.04
this was done on ubuntu Ubuntu 14.04.6 LTS on neweraws when clamd refused to use the
databases fetchec with freshclam:
~jean/src//clamav/clamav-0.102.4
did install g++ and ...
until ./configure --disable-clamonacc did produce a makefile
make -j2
worked
install with sudo make install everything come in /usr/local/ bin, lib ....
to execute these commands you need
jean@ip-172-30-0-100-neweraws:/usr/local/bin$ export LD_LIBRARY_PATH=/usr/local/lib/:$LD_LIBRARY_PATH
jean@ip-172-30-0-100-neweraws:/usr/local/bin$ ./freshclam --help
Clam AntiVirus: Database Updater 0.102.4
By The ClamAV Team: https://www.clamav.net/about.html#credits
(C) 2020 Cisco Systems, Inc.
freshclam [options]
--help -h Show this help
--version -V Print version number and exit
--verbose -v Be verbose
--debug Enable debug messages
--quiet Only output error messages
--no-warnings Don't print and log warnings
....
After a long debugging session if found clamd crashes at start with :# cat /var/log/clamav/clamav.logMy guess clamd builds all the virus signatures in memory and our system only has less than 1 Gb free memory.
...
Fri Jul 24 15:31:12 2020 -> clamd daemon 0.102.4 (OS: linux-gnu, ARCH: x86_64, CPU: x86_64) Fri Jul 24 15:31:12 2020 -> Log file size limited to 4294967295 bytes. Fri Jul 24 15:31:12 2020 -> Reading databases from /var/lib/clamav Fri Jul 24 15:31:12 2020 -> Not loading PUA signatures. Fri Jul 24 15:31:12 2020 -> Bytecode: Security mode set to "TrustSigned". Fri Jul 24 15:32:01 2020 -> Loaded 8190032 signatures. Fri Jul 24 15:32:04 2020 -> LOCAL: Unix socket file /var/run/clamav/clamd.ctl Fri Jul 24 15:32:04 2020 -> LOCAL: Setting connection queue length to 15 Fri Jul 24 15:32:04 2020 -> ERROR: daemonize() failed: Cannot allocate memory Fri Jul 24 15:32:04 2020 -> Socket file removed.
documentation used : https://help.ubuntu.com/community/PostfixGreylisting
Installation
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# apt install postgrey
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following package was automatically installed and is no longer required:
libmilter1.0.1
Use 'apt autoremove' to remove it.
The following additional packages will be installed:
libnet-rblclient-perl libparse-syslog-perl
The following NEW packages will be installed:
libnet-rblclient-perl libparse-syslog-perl postgrey
0 upgraded, 3 newly installed, 0 to remove and 0 not upgraded.
Need to get 75.3 kB of archives.
After this operation, 265 kB of additional disk space will be used.
dapt postfix:
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# postconf smtpd_client_restrictions
smtpd_client_restrictions = permit_sasl_authenticated
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# postconf -e 'smtpd_client_restrictions=permit_sasl_authenticated, check_policy_service inet:127.0.0.1:10023'
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# postconf smtpd_client_restrictions
smtpd_client_restrictions = permit_sasl_authenticated, check_policy_service inet:127.0.0.1:10023
root@ip-172-30-0-137-aws:/etc/amavis/conf.d# systemctl restart postfix
root@ip-172-30-0-137-aws:/etc/amavis/conf.d#
When we try to deliver mail:
jean@ip-172-30-0-100-neweraws:/etc/amavis/conf.d$ telnet aws.huens.be 25 Trying 34.245.218.107... Connected to aws.huens.be. Escape character is '^]'. 220 aws.huens.be ESMTP Postfix (Ubuntu) HELO neweraws.huens.be 250 aws.huens.be MAIL from: <jean@huens.be> 250 2.1.0 Ok RCPT to: <jean@aws.huens.be> 450 4.2.0 <neweraws.christiaens.org[52.16.59.195]>: Client host rejected: Greylisted, see http://postgrey.schweikert.ch/help/aws.huens.be.html quit 221 2.0.0 Bye Connection closed by foreign host. jean@ip-172-30-0-100-neweraws:/etc/amavis/conf.d$
After changing /etc/defaults/postgrey we get:
RCPT to: <xtof@aws.huens.be>
450 4.2.0 <neweraws.christiaens.org[52.16.59.195]>: Client host rejected: aws.huens.be greylisted for 300 seconds
Configuration changes: whitelisting clients:
root@ip-172-30-0-137-aws:/etc/postgrey# vi whitelist_clients.local root@ip-172-30-0-137-aws:/etc/postgrey# systemctl restart postgrey
# postgrey whitelist for mail client hostnames .local # -------------------------------------------- # Added for christiaens.org, huygens.biz, ps23.be, .... # allow our AWS public IP #54.49.255.158 52.16.59.195 # and our mailforwarders 134.58.40.2 # hermes2.cs.kuleuven.be MX for us 134.58.40.3 ....
TODO complete the whitelisting.clients and clients.local
documentation: http://www.postfix.org/VIRTUAL_README.html#canonical
We first setup for virtual domains (will be used finally)
Now all mail for huens.be is handled locally.
I did not find how I can tell postfix to deliver huens.be to another host it allways seems
to do at least user validation ? ...
But mapped users are handled correctly and delivered to the new address:
jeanke@huens.be jean.huens@cs.kuleuven.be
To relay mails for other domains:
root@ip-172-30-0-137-aws:~# postconf -d relay_domains
relay_domains = ${{$compatibility_level} < {2} ? {$mydestination} : {}}
root@ip-172-30-0-137-aws:~# postconf -e 'relay_domains=hash:/etc/postfix/relay_domains'
root@ip-172-30-0-137-aws:~# cd /etc/postfix
root@ip-172-30-0-137-aws:/etc/postfix# vi relay_domains
root@ip-172-30-0-137-aws:/etc/postfix# postmap -u relay_domains
root@ip-172-30-0-137-aws:/etc/postfix# cat relay_domains
#
# these are domain for which we relay mail
# to prevent next warning add a comment after each domain:
# postmap: warning: relay_domains, line 2: expected format: key whitespace value
ps23.be #ps23.be domain
This can only be done after letsencrypt is installed and config
I did use https://upcloud.com/community/tutorials/secure-postfix-using-lets-encrypt/ as
guide
Initial postfix setup:
smtpd_tls_cert_file = /etc/letsencrypt/live/www2.huens.be/fullchain.pem
smtpd_tls_key_file = /etc/ssl/private/ssl-cert-snakeoil.key
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_sasl_local_domain =
smtpd_sasl_security_options = noanonymous
smtpd_sasl_tls_security_options = $smtpd_sasl_security_options
broken_sasl_auth_clients = no
smtpd_sasl_auth_enable = yes
smtpd_recipient_restrictions = , check_policy_service unix:private/policy-spf
smtp_tls_security_level =
smtpd_tls_security_level =
smtp_tls_note_starttls_offer = no
smtpd_tls_loglevel = 0
smtpd_tls_received_header = no
virtual_alias_domains = huens.be
Config for letsencrypt:
root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_tls_cert_file = /etc/letsencrypt/live/www2.huens.be/fullchain.pem' root@ip-172-30-0-137-aws:~# postconf -e 'smtpd_tls_key_file = /etc/letsencrypt/live/www2.huens.be/privkey.pem' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_sasl_type = dovecot' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_sasl_path = private/auth' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_sasl_local_domain =www2.huens.be' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_sasl_security_options = noanonymous' root@ip-172-30-0-137-aws:/# postconf -e 'broken_sasl_auth_clients = yes' root@ip-172-30-0-137-aws:/# postconf -e 'broken_sasl_auth_clients = yes' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_sasl_auth_enable = yes' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination, check_policy_service unix:private/policy-spf' root@ip-172-30-0-137-aws:/# postconf -e 'smtp_tls_security_level = may' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_tls_security_level = may' root@ip-172-30-0-137-aws:/# postconf -e 'smtp_tls_note_starttls_offer = yes' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_tls_loglevel = 1' root@ip-172-30-0-137-aws:/# postconf -e 'smtpd_tls_received_header = yes' root@ip-172-30-0-137-aws:/# postconf -e 'virtual_alias_domains = huens.be,christaens.org,huygens.biz,ps23.be,jsfoundation.be,karenchristiaens.com'After editing /etc/postfix/virtual :
root@ip-172-30-0-137-aws:~# vi /etc/postfix/virtual root@ip-172-30-0-137-aws:~# sudo postmap /etc/postfix/virtual root@ip-172-30-0-137-aws:~# sudo systemctl restart postfix root@ip-172-30-0-137-aws:~# systemctl status postfix ● postfix.service - Postfix Mail Transport Agent Loaded: loaded (/lib/systemd/system/postfix.service; enabled; vendor preset: enabled) Active: active (exited) since Fri 2019-12-20 15:54:48 UTC; 9s ago Process: 24270 ExecStart=/bin/true (code=exited, status=0/SUCCESS) Main PID: 24270 (code=exited, status=0/SUCCESS) Dec 20 15:54:48 ip-172-30-0-137-aws systemd[1]: Starting Postfix Mail Transport Agent... Dec 20 15:54:48 ip-172-30-0-137-aws systemd[1]: Started Postfix Mail Transport Agent.To make postfix use 465
root@ip-172-30-0-137-aws:/etc/postfix# diff master.cf master.cf.201905241531
29,33c29,32
< # does this start smtp on 465 ? jean
< smtps inet n - y - - smtpd
< -o syslog_name=postfix/smtps
< -o smtpd_tls_wrappermode=yes
< -o smtpd_sasl_auth_enable=yes
---
> #smtps inet n - y - - smtpd
> # -o syslog_name=postfix/smtps
> # -o smtpd_tls_wrappermode=yes
> # -o smtpd_sasl_auth_enable=yes
68,69c67
< # not sure on next line when uncommented there is something on 465 but no tls
< #smtps inet n - y - - smtpd
---
> smtps inet n - y - - smtpd
root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# diff 10-ssl.conf 10-ssl.conf.ORG
12,13c12,13
< ssl_cert = </etc/letsencrypt/live/www2.huens.be/fullchain.pem
< ssl_key = </etc/letsencrypt/live/www2.huens.be/privkey.pem
---
> ssl_cert = </etc/dovecot/private/dovecot.pem
> ssl_key = </etc/dovecot/private/dovecot.key
50d49
< ssl_protocols = !SSLv2 !SSLv3
root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# diff 10-master.conf 10-master.conf.ORG
22,23c22,23
< port = 993
< ssl = yes
---
> #port = 993
> #ssl = yes
89,93c89,93
< ## unix_listener auth-userdb {
< ## #mode = 0666
< ## #user =
< ## #group =
< ## }
---
> unix_listener auth-userdb {
> #mode = 0666
> #user =
> #group =
> }
99,104d98
< unix_listener /var/spool/postfix/private/auth {
< mode = 0660
< # Assuming the default Postfix user and group
< user = postfix
< group = postfix
< }
This is a technique to rsync info from the previous to the new server. It is only needed during the conversion period.
Users can be transferred from revious server by copying lines from /etc/passwd, /etc/group,
/etc/shadow.
Beware for duplicate uid, gid ....
To give root access from the source server to the destination server:
Generate a key on the destination server:
# export HOME=/root
# ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase): some good pass phrase
Enter same passphrase again: some good pass phrase
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:.........
The key's randomart image is:
+---[RSA .....
.....
......
# ls -l /root/.ssh/
total 12
-rw------- 1 root root 554 May 12 16:51 authorized_keys
-rw------- 1 root root 1679 Sep 10 10:12 id_rsa
-rw-r--r-- 1 root root 406 Sep 10 10:12 id_rsa.pub
Copy the public key /root/.ssh/id_rsa.pub on the target server: to /root/.ssh/authorized_keys on the source server
Now root on the destination server has root access to the target server. You need to know the pass phrase !
To transfer directories from the source server :
# rsync -v --update --recursive --links --perms --times --group --owner --devices --specials --one-file-system --hard-links
neweraws.huens.be:/root/bin/ /root/bin
Enter passphrase for key '/root/.ssh/id_rsa':
receiving incremental file list
created directory /root/bin
./
check_soa
check_soa.pl
check_soa_all
checkaliases
digspf
dorsync_home
dorsync_home.ORG
local_rsync
rsync.sh
sent 202 bytes received 10,666 bytes 557.33 bytes/sec
total size is 9,974 speedup is 0.92
root@ip-172-30-0-137-aws:~#
To ease transfer there is a transfer_from_previous command in /root/bin. It uses rsync; See below (apache web server) for its use.
Install
root@ip-172-30-0-137-aws:/etc/postfix# apt install apache2
....
root@ip-172-30-0-137-aws:/etc/postfix# systemctl status apache2
● apache2.service - The Apache HTTP Server
Loaded: loaded (/lib/systemd/system/apache2.service; enabled; vendor preset: enabled)
Drop-In: /lib/systemd/system/apache2.service.d
└─apache2-systemd.conf
Active: active (running) since Fri 2019-05-31 15:03:30 UTC; 2min 10s ago
Main PID: 8866 (apache2)
Tasks: 55 (limit: 2362)
CGroup: /system.slice/apache2.service
├─8866 /usr/sbin/apache2 -k start
├─8868 /usr/sbin/apache2 -k start
└─8869 /usr/sbin/apache2 -k start
May 31 15:03:30 ip-172-30-0-137-aws systemd[1]: Starting The Apache HTTP Server...
May 31 15:03:30 ip-172-30-0-137-aws apachectl[8841]: AH00558: apache2: Could not reliably determine the server
May 31 15:03:30 ip-172-30-0-137-aws systemd[1]: Started The Apache HTTP Server.
todo: use /var/wwwserver (allows later use of separate disk for www)
:~/bin# ./transfer_from_previous /var/wwwserver /var/
Enter passphrase for key '/root/.ssh/id_rsa':
~/bin# ls -l /var/wwwserver
total 8
drwxr-xr-x 6 root root 4096 Nov 13 2003 local
drwxr-xr-x 2 root root 4096 Jan 17 2008 public_html
~/bin# du -s /var/wwwserver
1147108 /var/wwwserver
# diff apache2.conf apache2.conf.ORG 89,92d88 < # attempt to solve following error < # AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using 172.30.0.137.
# Set the 'ServerName' directive globall#y < Servername aws.huens.be < 178,184d173 < </Directory> < < # we also use /var/wwwserver < <Directory /var/wwwserver/> < Options Indexes FollowSymLinks < AllowOverride None < Require all granted
As installed we get following error at apache startup (and the webserver is unreachable:
Sep 22 06:25:02 ip-172-30-0-137-aws systemd[1]: Reloading The Apache HTTP Server. Sep 22 06:25:02 ip-172-30-0-137-aws apachectl[1838]: AH00558: apache2: Could not reliably
determine the server's fully qualified domain name, using 172.30.0.137.
Set the 'ServerName' directive globally
This solution is already included above (2.12.1)
Enable sitesis done based on old config.
The aapache2 virtual hosts mechanism is based on the hostname in the request. We have made
www2.christiaens.org, www2.huens.be, www2.huygens.biz, www2.karenchristiaens.com www2.ps23.be and www2.purpur.be with A the IP op our current server (34.244.141.182).
And in the config files:
root@ip-172-30-0-137-aws:/etc/apache2# grep www2 /etc/apache2/sites-enabled/*.conf
/etc/apache2/sites-enabled/christiaens.org.conf:ServerName www2.christiaens.org
/etc/apache2/sites-enabled/huens.be.conf: ServerName www2.huens.be
/etc/apache2/sites-enabled/huygens.biz.conf: ServerName www2.huygens.biz
/etc/apache2/sites-enabled/karenchristiaens.com.conf: ServerName www2.karenchristiaens.com
/etc/apache2/sites-enabled/ps23.be.conf: ServerName www2.ps23.be
/etc/apache2/sites-enabled/purpur.be.conf: ServerName www2.purpur.be
This makes http://www.huens.be etc. work.Install certbot:
root@ip-172-30-0-137-aws:/etc/apache2# apt install python-certbot-apache Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: linux-aws-headers-4.15.0-1048 linux-aws-headers-4.15.0-1050 linux-aws-headers-4.15.0-1051 linux-aws-headers-4.15.0-1052 Use 'apt autoremove' to remove them. The following additional packages will be installed: augeas-lenses certbot libaugeas0 libpython-stdlib python python-minimal python-pyicu python2.7 python2.7-minimal python3-acme python3-augeas python3-certbot python3-certbot-apache python3-configargparse python3-future python3-josepy python3-lib2to3 python3-mock python3-parsedatetime python3-pbr python3-requests-toolbelt python3-rfc3339 python3-tz python3-zope.component python3-zope.event python3-zope.hookable Suggested packages: augeas-doc python3-certbot-nginx python-certbot-doc augeas-tools python-doc python-tk python2.7-doc binfmt-support python-acme-doc python-certbot-apache-doc python-future-doc python-mock-doc The following NEW packages will be installed: augeas-lenses certbot libaugeas0 libpython-stdlib python python-certbot-apache python-minimal python-pyicu python2.7 python2.7-minimal python3-acme python3-augeas python3-certbot python3-certbot-apache python3-configargparse python3-future python3-josepy python3-lib2to3 python3-mock python3-parsedatetime python3-pbr python3-requests-toolbelt python3-rfc3339 python3-tz python3-zope.component python3-zope.event python3-zope.hookable 0 upgraded, 27 newly installed, 0 to remove and 0 not upgraded. Need to get 3,402 kB of archives. After this operation, 14.5 MB of additional disk space will be used. Do you want to continue? [Y/n] y Get:1 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic-updates/main amd64 python2.7-minimal amd64 2.7.15-4ubuntu4~18.04.2 [1,296 kB] ... Get:27 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic/universe amd64 python-certbot-apache all 0.23.0-1 [1,692 B] Fetched 3,402 kB in 1s (5,548 kB/s) Selecting previously unselected package python2.7-minimal. (Reading database ... 193729 files and directories currently installed.) Preparing to unpack .../python2.7-minimal_2.7.15-4ubuntu4~18.04.2_amd64.deb ... Unpacking python2.7-minimal (2.7.15-4ubuntu4~18.04.2) ... Selecting previously unselected package python-minimal. Preparing to unpack .../python-minimal_2.7.15~rc1-1_amd64.deb ... Unpacking python-minimal (2.7.15~rc1-1) ... Selecting previously unselected package python2.7. Preparing to unpack .../python2.7_2.7.15-4ubuntu4~18.04.2_amd64.deb ... Unpacking python2.7 (2.7.15-4ubuntu4~18.04.2) ... Selecting previously unselected package libpython-stdlib:amd64. Preparing to unpack .../libpython-stdlib_2.7.15~rc1-1_amd64.deb ... Unpacking libpython-stdlib:amd64 (2.7.15~rc1-1) ... Setting up python2.7-minimal (2.7.15-4ubuntu4~18.04.2) ... Linking and byte-compiling packages for runtime python2.7... Setting up python-minimal (2.7.15~rc1-1) ... Selecting previously unselected package python. (Reading database ... 193786 files and directories currently installed.) Preparing to unpack .../00-python_2.7.15~rc1-1_amd64.deb ... ... Setting up python3-pbr (3.1.1-3ubuntu3) ... update-alternatives: using /usr/bin/python3-pbr to provide /usr/bin/pbr (pbr) in auto mode Setting up python3-mock (2.0.0-3) ... Setting up python3-zope.event (4.2.0-1) ... Setting up python2.7 (2.7.15-4ubuntu4~18.04.2) ... Setting up libpython-stdlib:amd64 (2.7.15~rc1-1) ... Setting up python3-configargparse (0.11.0-1) ... Setting up python3-zope.hookable (4.0.4-4build4) ... Setting up augeas-lenses (1.10.1-2) ... Setting up python3-josepy (1.1.0-1) ... Setting up python3-lib2to3 (3.6.9-1~18.04) ... Setting up python3-tz (2018.3-2) ... Setting up python (2.7.15~rc1-1) ... Setting up python-pyicu (1.9.8-0ubuntu1) ... Setting up python3-rfc3339 (1.0-4) ... Setting up python3-zope.component (4.3.0-1) ... Setting up libaugeas0:amd64 (1.10.1-2) ... Setting up python3-future (0.15.2-4ubuntu2) ... update-alternatives: using /usr/bin/python3-futurize to provide /usr/bin/futurize (futurize) in auto mode update-alternatives: using /usr/bin/python3-pasteurize to provide /usr/bin/pasteurize (pasteurize) in auto mode Setting up python3-augeas (0.5.0-1) ... Setting up python3-acme (0.31.0-2~ubuntu18.04.1) ... Setting up python3-parsedatetime (2.4-2) ... Setting up python3-certbot (0.27.0-1~ubuntu18.04.1) ... Setting up certbot (0.27.0-1~ubuntu18.04.1) ... Created symlink /etc/systemd/system/timers.target.wants/certbot.timer → /lib/systemd/system/certbot.timer. Setting up python3-certbot-apache (0.23.0-1) ... Setting up python-certbot-apache (0.23.0-1) ... Processing triggers for man-db (2.8.3-2ubuntu0.1) ... Processing triggers for mime-support (3.60ubuntu1) ... Processing triggers for libc-bin (2.27-3ubuntu1) ... root@ip-172-30-0-137-aws:/etc/apache2#Check apache config for virtual hosts:
root@ip-172-30-0-137-aws:/etc/apache2# grep ServerName /etc/apache2/sites-available/*.conf
/etc/apache2/sites-available/000-default.conf: # The ServerName directive sets the request scheme, hostname and port that
/etc/apache2/sites-available/000-default.conf: # redirection URLs. In the context of virtual hosts, the ServerName
/etc/apache2/sites-available/000-default.conf: #ServerName www.example.com
/etc/apache2/sites-available/christiaens.org.conf:#ServerName www.christiaens.org
/etc/apache2/sites-available/christiaens.org.conf:ServerName www2.christiaens.org
/etc/apache2/sites-available/christiaens.org.conf:# ServerName w3.christiaens.org
/etc/apache2/sites-available/huens.be.conf:# ServerName w3.huens.be
/etc/apache2/sites-available/huens.be.conf:# ServerName www.huens.be
/etc/apache2/sites-available/huens.be.conf:# ServerName aws.huens.be
/etc/apache2/sites-available/huens.be.conf: ServerName www2.huens.be
/etc/apache2/sites-available/huygens.biz.conf: ServerName www2.huygens.biz
/etc/apache2/sites-available/huygens.biz.conf:#test ServerName www.huygens.biz
/etc/apache2/sites-available/jsfoundation.be.conf: ServerName repo2.jsfoundation.be
/etc/apache2/sites-available/jsfoundation.be.conf:# ServerName w3.ps23.be
/etc/apache2/sites-available/karenchristiaens.com.conf: ServerName www2.karenchristiaens.com
/etc/apache2/sites-available/ps23.be.conf: ServerName www2.ps23.be
/etc/apache2/sites-available/ps23.be.conf:# ServerName w3.ps23.be
/etc/apache2/sites-available/purpur.be.conf: ServerName www2.purpur.be
/etc/apache2/sites-available/purpur.be.conf:# ServerName w3.purpur.be
The commented out lines are from the original server
Start certbot
The use of certbot is obstructed by dns problems (mainly due to glue records to obsolete
xname.org servers)
root@ip-172-30-0-137-aws:/etc/apache2/mods-enabled# sudo certbot --apache -d www2.huens.be -d www2.huygens.biz -d www2.christiaens.org -d www2.ps23.be -d www2.purpur.be Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator apache, Installer apache Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): jean@huens.be - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: n Obtaining a new certificate Performing the following challenges: http-01 challenge for www2.christiaens.org http-01 challenge for www2.huens.be http-01 challenge for www2.huygens.biz http-01 challenge for www2.ps23.be http-01 challenge for www2.purpur.be Waiting for verification... Cleaning up challenges Failed authorization procedure. www2.purpur.be (http-01): urn:ietf:params:acme:error:dns :: DNS problem: NXDOMAIN looking up A for www2.purpur.be, www2.christiaens.org (http-01): urn:ietf:params:acme:error:dns :: No valid IP addresses found for www2.christiaens.org IMPORTANT NOTES: - The following errors were reported by the server: Domain: www2.purpur.be Type: None Detail: DNS problem: NXDOMAIN looking up A for www2.purpur.be Domain: www2.christiaens.org Type: None Detail: No valid IP addresses found for www2.christiaens.org - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal.
After removing domains with dns problems:
root@ip-172-30-0-137-aws:/etc/apache2/mods-enabled# sudo certbot --apache -d www2.huens.be -d www2.huygens.biz Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator apache, Installer apache Obtaining a new certificate Performing the following challenges: http-01 challenge for www2.huens.be http-01 challenge for www2.huygens.biz Waiting for verification... Cleaning up challenges Created an SSL vhost at /etc/apache2/sites-available/huens.be-le-ssl.conf Enabled Apache socache_shmcb module Enabled Apache ssl module Deploying Certificate to VirtualHost /etc/apache2/sites-available/huens.be-le-ssl.conf Enabling available site: /etc/apache2/sites-available/huens.be-le-ssl.conf Created an SSL vhost at /etc/apache2/sites-available/huygens.biz-le-ssl.conf Deploying Certificate to VirtualHost /etc/apache2/sites-available/huygens.biz-le-ssl.conf Enabling available site: /etc/apache2/sites-available/huygens.biz-le-ssl.conf Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://www2.huens.be and https://www2.huygens.biz You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=www2.huens.be https://www.ssllabs.com/ssltest/analyze.html?d=www2.huygens.biz - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/www2.huens.be/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/www2.huens.be/privkey.pem Your cert will expire on 2020-03-14. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le root@ip-172-30-0-137-aws:/etc/
Test renewal
root@ip-172-30-0-137-aws:~# sudo certbot renew --dry-run Saving debug log to /var/log/letsencrypt/letsencrypt.log - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Processing /etc/letsencrypt/renewal/www2.huens.be.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Cert not due for renewal, but simulating renewal for dry run Plugins selected: Authenticator apache, Installer apache Renewing an existing certificate Performing the following challenges: http-01 challenge for www2.huens.be http-01 challenge for www2.huygens.biz Waiting for verification... Cleaning up challenges - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - new certificate deployed with reload of apache server; fullchain is /etc/letsencrypt/live/www2.huens.be/fullchain.pem - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates below have not been saved.) Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/www2.huens.be/fullchain.pem (success) ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates above have not been saved.) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. root@ip-172-30-0-137-aws:~# du -s /etc/letsencrypt 160 /etc/letsencrypt
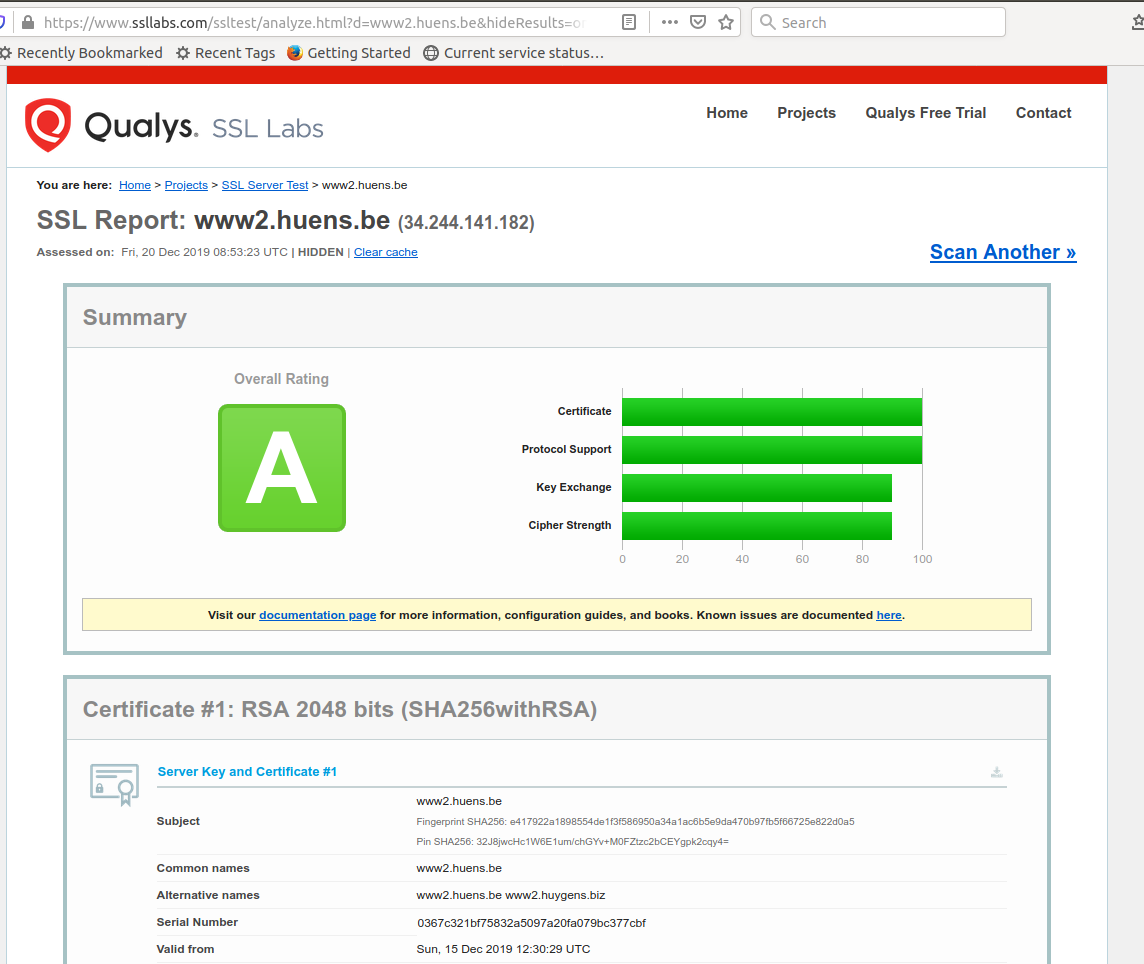
Test on SSL Labs (https://www.ssllabs.com/ssltest/analyze.html?d=www2.huens.be) report
support for TLS 1.0 and TLS 1.1.
To stop support for TLS 1.0 and TLS 1.1:
root@ip-172-30-0-137-aws:/etc/letsencrypt# diff /etc/apache2/mods-available/ssl.conf /etc/apache2/mods-available/ssl.conf.ORG 59,61c59 < #SSLCipherSuite HIGH:!aNULL < # https://www.leaderssl.com/news/471-how-to-disable-outdated-versions-of-ssl-tls-in-apache < SSLCipherSuite HIGH:!aNULL:!MD5:!3DES --- > SSLCipherSuite HIGH:!aNULL 71,72d68 < # we prefer strong ciphers < SSLHonorCipherOrder on 77,79c73 < #SSLProtocol all -SSLv3 < # disable some protocols https://www.leaderssl.com/news/471-how-to-disable-outdated-versions-of-ssl-tls-in-apache < SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 --- > SSLProtocol all -SSLv3
There is per virtual host a conf file containing ssl info mainly for letsencrypt (donot change /etc/letsencrypt/ files!):
root@ip-172-30-0-137-aws:/etc/apache2/sites-available# diff huens.be-le-ssl.conf huens.be-le-ssl.conf.ORG 14,18d13 < # attempt to satisfy quallis ssl lab < # disable some protocols https://www.leaderssl.com/news/471-how-to-disable-outdated-versions-of-ssl-tls-in-apache < SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1 < # we prefer strong ciphers < SSLHonorCipherOrder on
After these changes ssllabs.com seems rather satisfied (improvements are possible by changing weak ciphers):

Extend certificates with new domains:
root@ip-172-30-0-137-aws:/etc/apache2/sites-available# certbot certonly --expand -d www2.huens.be -d www2.huygens.biz -d www2.christiaens.org -d www2.ps23.be -d www2.purpur.be -d mail2.huens.be Saving debug log to /var/log/letsencrypt/letsencrypt.log How would you like to authenticate with the ACME CA? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: Apache Web Server plugin - Beta (apache) 2: Spin up a temporary webserver (standalone) 3: Place files in webroot directory (webroot) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-3] then [enter] (press 'c' to cancel): 1 Plugins selected: Authenticator apache, Installer None Renewing an existing certificate Performing the following challenges: http-01 challenge for www2.huens.be http-01 challenge for www2.huygens.biz http-01 challenge for mail2.huens.be http-01 challenge for www2.christiaens.org http-01 challenge for www2.ps23.be http-01 challenge for www2.purpur.be Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/www2.huens.be/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/www2.huens.be/privkey.pem Your cert will expire on 2020-03-19. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le root@ip-172-30-0-137-aws:/etc/apache2/sites-available#
One cannot add domain names pointing to other/wrong IP numbers:
root@ip-172-30-0-137-aws:/etc/apache2/sites-available# certbot certonly --expand -d www2.huens.be -d www2.huygens.biz -d www2.christiaens.org -d www2.ps23.be -d www2.purpur.be -d mail2.huens.be -d mail.huens.be
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Apache Web Server plugin - Beta (apache)
2: Spin up a temporary webserver (standalone)
3: Place files in webroot directory (webroot)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-3] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator apache, Installer None
Renewing an existing certificate
Performing the following challenges:
http-01 challenge for mail2.huens.be
http-01 challenge for www2.christiaens.org
http-01 challenge for www2.huens.be
http-01 challenge for www2.huygens.biz
http-01 challenge for www2.ps23.be
http-01 challenge for www2.purpur.be
http-01 challenge for mail.huens.be
Waiting for verification...
Cleaning up challenges
Failed authorization procedure. mail.huens.be (http-01): urn:ietf:params:acme:error:unauthorized :: The client lacks sufficient authorization :: Invalid response from http://mail.huens.be/.well-known/acme-challenge/FhOu4lt63oSfBi3hEfLzP9hQADjEJgRQ-85NvKXpCVg [52.16.59.195]: "<!DOCTYPE HTML PUBLIC \"-//IETF//DTD HTML 2.0//EN\">\n<html><head>\n<title>404 Not Found</title>\n</head><body>\n<h1>Not Found</h1>\n<p"
IMPORTANT NOTES:
- The following errors were reported by the server:
Domain: mail.huens.be
Type: unauthorized
Detail: Invalid response from
http://mail.huens.be/.well-known/acme-challenge/FhOu4lt63oSfBi3hEfLzP9hQADjEJgRQ-85NvKXpCVg
[52.16.59.195]: "<!DOCTYPE HTML PUBLIC \"-//IETF//DTD HTML
2.0//EN\">\n<html><head>\n<title>404 Not
Found</title>\n</head><body>\n<h1>Not Found</h1>\n<p"
To fix these errors, please make sure that your domain name was
entered correctly and the DNS A/AAAA record(s) for that domain
contain(s) the right IP address.
This was done after dns problems with NS were cleared
To add the obtained certificate and update the apache configs:
root@ip-172-30-0-137-aws:/etc/apache2/sites-available# certbot --apache --expand -d www2.huens.be -d www2.huygens.biz -d www2.christiaens.org -d www2.ps23.be -d www2.purpur.be -d mail2.huens.be Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator apache, Installer apache Cert not yet due for renewal You have an existing certificate that has exactly the same domains or certificate name you requested and isn't close to expiry. (ref: /etc/letsencrypt/renewal/www2.huens.be.conf) What would you like to do? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: Attempt to reinstall this existing certificate 2: Renew & replace the cert (limit ~5 per 7 days) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1 Keeping the existing certificate Deploying Certificate to VirtualHost /etc/apache2/sites-enabled/huens.be-le-ssl.conf Deploying Certificate to VirtualHost /etc/apache2/sites-enabled/huygens.biz-le-ssl.conf Created an SSL vhost at /etc/apache2/sites-available/christiaens.org-le-ssl.conf Deploying Certificate to VirtualHost /etc/apache2/sites-available/christiaens.org-le-ssl.conf Enabling available site: /etc/apache2/sites-available/christiaens.org-le-ssl.conf Created an SSL vhost at /etc/apache2/sites-available/ps23.be-le-ssl.conf Deploying Certificate to VirtualHost /etc/apache2/sites-available/ps23.be-le-ssl.conf Enabling available site: /etc/apache2/sites-available/ps23.be-le-ssl.conf Created an SSL vhost at /etc/apache2/sites-available/purpur.be-le-ssl.conf Deploying Certificate to VirtualHost /etc/apache2/sites-available/purpur.be-le-ssl.conf Enabling available site: /etc/apache2/sites-available/purpur.be-le-ssl.conf We were unable to find a vhost with a ServerName or Address of mail2.huens.be. Which virtual host would you like to choose? (note: conf files with multiple vhosts are not yet supported) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: 000-default.conf | | | Enabled 2: jsfoundation.be.conf | Multiple Names | | Enabled 3: huens.be.conf | www2.huens.be | | Enabled 4: karenchristiaens.com.conf | Multiple Names | | Enabled 5: christiaens.org.conf | Multiple Names | | Enabled 6: huygens.biz.conf | Multiple Names | | Enabled 7: purpur.be.conf | Multiple Names | | Enabled 8: huens.be-le-ssl.conf | www2.huens.be | HTTPS | Enabled 9: huygens.biz-le-ssl.conf | Multiple Names | HTTPS | Enabled 10: ps23.be.conf | Multiple Names | | Enabled 11: christiaens.org-le-ssl.conf | Multiple Names | HTTPS | Enabled 12: ps23.be-le-ssl.conf | Multiple Names | HTTPS | Enabled 13: purpur.be-le-ssl.conf | Multiple Names | HTTPS | Enabled - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-13] then [enter] (press 'c' to cancel): 8 Deploying Certificate to VirtualHost /etc/apache2/sites-enabled/huens.be-le-ssl.conf Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 Redirecting vhost in /etc/apache2/sites-enabled/000-default.conf to ssl vhost in /etc/apache2/sites-enabled/huens.be-le-ssl.conf Redirecting vhost in /etc/apache2/sites-enabled/huygens.biz.conf to ssl vhost in /etc/apache2/sites-enabled/huygens.biz-le-ssl.conf Redirecting vhost in /etc/apache2/sites-enabled/christiaens.org.conf to ssl vhost in /etc/apache2/sites-available/christiaens.org-le-ssl.conf Redirecting vhost in /etc/apache2/sites-enabled/ps23.be.conf to ssl vhost in /etc/apache2/sites-available/ps23.be-le-ssl.conf Redirecting vhost in /etc/apache2/sites-enabled/purpur.be.conf to ssl vhost in /etc/apache2/sites-available/purpur.be-le-ssl.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://www2.huens.be, https://www2.huygens.biz, https://www2.christiaens.org, https://www2.ps23.be, https://www2.purpur.be, and https://mail2.huens.be You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=www2.huens.be https://www.ssllabs.com/ssltest/analyze.html?d=www2.huygens.biz https://www.ssllabs.com/ssltest/analyze.html?d=www2.christiaens.org https://www.ssllabs.com/ssltest/analyze.html?d=www2.ps23.be https://www.ssllabs.com/ssltest/analyze.html?d=www2.purpur.be https://www.ssllabs.com/ssltest/analyze.html?d=mail2.huens.be - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/www2.huens.be/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/www2.huens.be/privkey.pem Your cert will expire on 2020-03-19. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le root@ip-172-30-0-137-aws:/etc/apache2/sites-available#
Now the new certificate is installed
AND the files /etc/apache2/sites-available/ were created for sites in the cerbot -d options:
ddroot@ip-172-30-0-137-aws:/etc/apache2/sites-available# ls 000-default.conf huens.be-le-ssl.conf huygens.biz.conf ps23.be.conf christiaens.org-le-ssl.conf huens.be-le-ssl.conf.ORG jsfoundation.be.conf purpur.be-le-ssl.conf christiaens.org.conf huens.be.conf karenchristiaens.com.conf purpur.be.conf default-ssl.conf huygens.biz-le-ssl.conf ps23.be-le-ssl.conf
root@ip-172-30-0-137-aws:/etc/apache2/sites-available# certbot certonly --expand \
-d www2.huens.be -d www2.huygens.biz -d www2.christiaens.org -d www2.ps23.be -d www2.purpur.be \
-d mail2.huens.be -d www2.karenchristiaens.com -d www2.jsfoundation.be
root@ip-172-30-0-137-aws:/etc/apache2/sites-available# certbot --apache --expand \
-d www2.huens.be -d www2.huygens.biz -d www2.christiaens.org -d www2.ps23.be -d www2.purpur.be \
-d mail2.huens.be -d www2.karenchristiaens.com -d www2.jsfoundation.be
Default installation install /etc/cron.d/letsencrypt. It executes twice a day certbot -q
renew.
We donot find an indication that letsencrypt automatically restarts apache after obtaining a
new certicicate and the dovecot and postfix also use the letsencrypt live files.
Therefore we install :
root@ip-172-30-0-137-aws:/etc/letsencrypt# cp /root/bin/restart_after_renewal.sh /etc/letsencrypt/renewal-hooks/deploy/ root@ip-172-30-0-137-aws:/etc/letsencrypt# cat /etc/letsencrypt/renewal-hooks/deploy/restart_after_renewal.sh #! /bin/bash # restart_after_renewal.sh # # restart all services using a letsencrypt key after key renewal # apache is done automatically but we also need # postfix # dovecot # our domains # christiaens.org huens.be jsfoundation.be purpur.be # huygens.biz karenchristiaens.com ps23.be systemctl restart dovecot systemctl restart postfix # apache does not show in letscrypt config files systemctl restart apache2 # warn system admins echo "`hostname` `date` keys renewed " | mail -s "restart_after_renewal.sh executed" jean
jean@ip-172-30-0-137-aws:~$ sudo certbot renew --dry-run [sudo] password for jean: Sorry, try again. [sudo] password for jean: Saving debug log to /var/log/letsencrypt/letsencrypt.log - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Processing /etc/letsencrypt/renewal/www2.huens.be.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Cert not due for renewal, but simulating renewal for dry run Plugins selected: Authenticator apache, Installer None Renewing an existing certificate Performing the following challenges: http-01 challenge for mail2.huens.be http-01 challenge for www2.christiaens.org http-01 challenge for www2.huens.be http-01 challenge for www2.huygens.biz http-01 challenge for www2.jsfoundation.be http-01 challenge for www2.karenchristiaens.com http-01 challenge for www2.ps23.be http-01 challenge for www2.purpur.be Waiting for verification... Cleaning up challenges Dry run: skipping deploy hook command: /etc/letsencrypt/renewal-hooks/deploy/restart_after_renewal.sh - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - new certificate deployed without reload, fullchain is /etc/letsencrypt/live/www2.huens.be/fullchain.pem - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates below have not been saved.) Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/www2.huens.be/fullchain.pem (success) ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates above have not been saved.) - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Installation:
root@ip-172-30-0-137-aws:~# apt install bind9 bind9-doc bind9utils Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: linux-aws-headers-4.15.0-1037 linux-headers-4.15.0-1037-aws linux-image-4.15.0-1037-aws linux-modules-4.15.0-1037-aws Use 'apt autoremove' to remove them. The following additional packages will be installed: python3-ply Suggested packages: resolvconf python-ply-doc The following NEW packages will be installed: bind9 bind9-doc bind9utils python3-ply ....
Unpacking bind9 (1:9.11.3+dfsg-1ubuntu1.9) ... Selecting previously unselected package bind9-doc. Preparing to unpack .../bind9-doc_1%3a9.11.3+dfsg-1ubuntu1.9_all.deb ... Unpacking bind9-doc (1:9.11.3+dfsg-1ubuntu1.9) ... Setting up bind9-doc (1:9.11.3+dfsg-1ubuntu1.9) ... Setting up python3-ply (3.11-1) ... Setting up bind9utils (1:9.11.3+dfsg-1ubuntu1.9) ... Setting up bind9 (1:9.11.3+dfsg-1ubuntu1.9) ... Adding group `bind' (GID 126) ... Done. Adding system user `bind' (UID 120) ... Adding new user `bind' (UID 120) with group `bind' ... Not creating home directory `/var/cache/bind'. wrote key file "/etc/bind/rndc.key" Created symlink /etc/systemd/system/multi-user.target.wants/bind9.service → /lib/systemd/system/bind9.service. bind9-pkcs11.service is a disabled or a static unit, not starting it. bind9-resolvconf.service is a disabled or a static unit, not starting it. Processing triggers for man-db (2.8.3-2ubuntu0.1) ... Processing triggers for ufw (0.36-0ubuntu0.18.04.1) ... Processing triggers for ureadahead (0.100.0-21) ... Processing triggers for systemd (237-3ubuntu10.28) ... root@ip-172-30-0-137-aws:~#
# we store secondaries in /etc/bind/extern.slave
/etc/bind/extern.slave/** rw,
Storing secondaries elsewere is probably better.....Ubuntu 18.04 uses a configuration were /etc/resolv.conf is generated by systemd-resolv and it
config files.
The main config file seems /etc/systemd/resolved.conf :
# cat /etc/systemd/resolved.conf # This file is part of systemd. # # systemd is free software; you can redistribute it and/or modify it # under the terms of the GNU Lesser General Public License as published by # the Free Software Foundation; either version 2.1 of the License, or # (at your option) any later version. # # Entries in this file show the compile time defaults. # You can change settings by editing this file. # Defaults can be restored by simply deleting this file. # # See resolved.conf(5) for details [Resolve] #DNS= #FallbackDNS= #Domains= #LLMNR=no #MulticastDNS=no #DNSSEC=no #Cache=yes #DNSStubListener=yes
To check the status :
# systemd-resolve --status
Global
DNSSEC NTA: 10.in-addr.arpa
16.172.in-addr.arpa
168.192.in-addr.arpa
17.172.in-addr.arpa
18.172.in-addr.arpa
19.172.in-addr.arpa
20.172.in-addr.arpa
21.172.in-addr.arpa
22.172.in-addr.arpa
23.172.in-addr.arpa
24.172.in-addr.arpa
25.172.in-addr.arpa
26.172.in-addr.arpa
27.172.in-addr.arpa
28.172.in-addr.arpa
29.172.in-addr.arpa
30.172.in-addr.arpa
31.172.in-addr.arpa
corp
d.f.ip6.arpa
home
internal
intranet
lan
local
private
test
Link 2 (eth0)
Current Scopes: DNS
LLMNR setting: yes
MulticastDNS setting: no
DNSSEC setting: no
DNSSEC supported: no
DNS Servers: 172.30.0.2
DNS Domain: eu-west-1.compute.internal
# cat /etc/resolv.conf
# This file is managed by man:systemd-resolved(8). Do not edit.
#
# This is a dynamic resolv.conf file for connecting local clients to the
# internal DNS stub resolver of systemd-resolved. This file lists all
# configured search domains.
#
# Run "systemd-resolve --status" to see details about the uplink DNS servers
# currently in use.
#
# Third party programs must not access this file directly, but only through the
# symlink at /etc/resolv.conf. To manage man:resolv.conf(5) in a different way,
# replace this symlink by a static file or a different symlink.
#
# See man:systemd-resolved.service(8) for details about the supported modes of
# operation for /etc/resolv.conf.
nameserver 127.0.0.53
options edns0
search eu-west-1.compute.internal
To use local bind9 server :
# cat /etc/systemd/resolved.conf # This file is part of systemd. # # systemd is free software; you can redistribute it and/or modify it # under the terms of the GNU Lesser General Public License as published by # the Free Software Foundation; either version 2.1 of the License, or # (at your option) any later version. # # Entries in this file show the compile time defaults. # You can change settings by editing this file. # Defaults can be restored by simply deleting this file. # # See resolved.conf(5) for details [Resolve] #DNS= DNS=127.0.0.1 127.0.0.53 #FallbackDNS= FallbackDNS=8.8.8.8 #Domains= #LLMNR=no #MulticastDNS=no #DNSSEC=no #Cache=yes #DNSStubListener=yes
Verification
# systemd-resolve --status
Global
DNS Servers: 127.0.0.1
DNSSEC NTA: 10.in-addr.arpa
16.172.in-addr.arpa
168.192.in-addr.arpa
17.172.in-addr.arpa
18.172.in-addr.arpa
19.172.in-addr.arpa
20.172.in-addr.arpa
21.172.in-addr.arpa
22.172.in-addr.arpa
23.172.in-addr.arpa
24.172.in-addr.arpa
25.172.in-addr.arpa
26.172.in-addr.arpa
27.172.in-addr.arpa
28.172.in-addr.arpa
29.172.in-addr.arpa
30.172.in-addr.arpa
31.172.in-addr.arpa
corp
d.f.ip6.arpa
home
internal
intranet
lan
local
private
test
Link 2 (eth0)
Current Scopes: DNS
LLMNR setting: yes
MulticastDNS setting: no
DNSSEC setting: no
DNSSEC supported: no
DNS Servers: 172.30.0.2
DNS Domain: eu-west-1.compute.internal
# cat /etc/resolv.conf
# This file is managed by man:systemd-resolved(8). Do not edit.
...
# operation for /etc/resolv.conf.
nameserver 127.0.0.53
options edns0
search eu-west-1.compute.internal
It is not clear to me
Some mail domains e.g. hotmail.com easily blacklist mailsites on AWS. To solve this problem
we deliver mails for these domains through Amazon SES (Simple Email Service).
SES is setup to handle all your mail but we deliver only part of our mail flow.
For every domain you need
We only want to sent some domains over Amazon SES over an ssl encrypted session
Transport:
# cat transport # transport map for special cases # 20200822 amazon heeft purpur.be uit de sandbox gehaald hotmail.com smtp:[email-smtp.eu-west-1.amazonaws.com]:587 outlook.com smtp:[email-smtp.eu-west-1.amazonaws.com]:587 simulator.amazonses.com smtp:[email-smtp.eu-west-1.amazonaws.com]:587
Saslpasswd:
# cat sasl_passwd #Targethost:port user:password [email-smtp.eu-west-1.amazonaws.com]:587 AKINOTREALUSER43:BCTIS_ISNOT_The_REAL_passwdTYf
Cs.kuleuven.be did stop its mx email server backup service on december 2022. (Central ICTS does not support service.).
After filling this form i got :
What is already wrong :
I did subscribe to the list
Options for list subscription at http://mailman.junkemailfilter.com/options/mxbackup (login
needed)
whitelist and avoid rate limiting on email with a reverse IP address of *.junkemailfilter.com
/etc/postgrey/whitelist_clients:
# and our mailforwarders #junkemailfilter.com # NetRange: 184.105.182.0 - 184.105.182.255 ##CIDR: 184.105.182.0/24 #NetName: HURRICANE-CE2644-B869B600 #NetHandle: NET-184-105-182-0-1 #Parent: HURRICANE-11 (NET-184-104-0-0-1) #NetType: Reallocated #OriginAS: AS6939 #Organization: Junk Email Filter Inc. (JUNKE) #RegDate: 2011-04-22 #Updated: 2011-04-22 #Comment: ADDRESSES WITHIN THIS BLOCK ARE NON-PORTABLE #Ref: https://rdap.arin.net/registry/ip/184.105.182.0 # they prefer all ip of *.junkemailfilter.com # I assume this is 184.105.182.0/24
...
huens.be. MX 10 mail.huens.be. huens.be. MX 20 mxbackup1.junkemailfilter.com. huens.be. MX 30 mxbackup2.junkemailfilter.com.
...
huens.be. TXT "v=spf1 ip4:52.16.59.195 ip4:34.246.199.6 a:mxbackup1.junkemailfilter.com a:mxbackup2.junkemailfilter.com include:amazonses.com -all" huens.be. SPF "v=spf1 ip4:52.16.59.195 ip4:34.246.199.6 a:mxbackup1.junkemailfilter.com a:mxbackup2.junkemailfilter.com include:amazonses.com -all"
...
Deliver domain not related to mxbackup1.junkemailfilter.com
root@ip-172-30-0-137-aws:/home/jean# telnet mxbackup1.junkemailfilter.com 25 Trying 184.105.182.149... Connected to mxbackup1.junkemailfilter.com. Escape character is '^]'. 220 mxbackup.junkemailfilter.com ESMTP helo ikke 250 mxbackup.junkemailfilter.com Hello neweraws.christiaens.org [52.16.59.195] mail from: jean@huens.be 250 OK rcpt to: postmaster@loveofnature.world 250 Accepted data 354 Enter message, ending with "." on a line by itself mail from: jean@huens.be rcpt to: postmaster@loveofnature.world Date: Fri, 11 Nov 2022 16:01:11 +0100 subject: test via mxbackup1 komt dit erdoor ? . 550-REJECTED - MULTI-BLACKLIST - [S=3 - hostkarma.junkemailfilter.com] - 550-NoHeloHost NoHeloPeriod SenderNoA DOB-SENDER DOB-Helo NewKarma BlList - 550-ID=31922-25126 X=mxbackup H=neweraws.christiaens.org [52.16.59.195]:42886 550 HELO=[ikke] SN=[jean@huens.be] T=[postmaster@loveofnature.world] FR=[] S=[] quit 221 mxbackup.junkemailfilter.com closing connection Connection closed by foreign host.
Mail is not delivered
Deliver domain with MX to mxbackup1.junkemailfilter.com primary is up
root@ip-172-30-0-137-aws:/home/jean# telnet mxbackup1.junkemailfilter.com 25 Trying 184.105.182.149... Connected to mxbackup1.junkemailfilter.com. Escape character is '^]'. 220 mxbackup.junkemailfilter.com ESMTP HELO ikke 250 mxbackup.junkemailfilter.com Hello neweraws.christiaens.org [52.16.59.195] Mail from: Jean@huens.be 250 OK RCPT to postmaster@huens.be 500 unrecognized command RCPT to: postmaster@huens.be 250 Accepted data 354 Enter message, ending with "." on a line by itself Mail from: Jean@huens.be RCPT to postmaster@huens.be subject: test via mxbackup1 komt dit erdoor ? . 550-REJECTED - MULTI-BLACKLIST - [S=3 - hostkarma.junkemailfilter.com] - 550-NoHeloHost NoHeloPeriod SenderNoA DOB-SENDER DOB-Helo NewKarma BlList - 550-ID=32393-5952 X=mxbackup H=neweraws.christiaens.org [52.16.59.195]:34096 550 HELO=[ikke] SN=[Jean@huens.be] T=[postmaster@huens.be] FR=[] S=[] quit 221 mxbackup.junkemailfilter.com closing connection Connection closed by foreign host.
Did not figure out exactly why this is refused but mail from gmail when mail.huens.be is down passes.
 O
O
Secondary can not be used to enter unchecked mail.
Deliver domain jean@ps23.be with MX to mxbackup1.junkemailfilter.com primary is down
Unattended upgrade returned: True Packages that were upgraded: apt apt-utils libapt-inst2.0 libapt-pkg5.0 libexpat1 Packages that were kept from being auto-removed: linux-modules-4.15.0-1039-aws Package installation log: Log started: 2019-09-13 06:06:18 Preparing to unpack .../libapt-inst2.0_1.6.12_amd64.deb ... Unpacking libapt-inst2.0:amd64 (1.6.12) over (1.6.11) ... Setting up libapt-inst2.0:amd64 (1.6.12) ... Processing triggers for libc-bin (2.27-3ubuntu1) ... Log ended: 2019-09-13 06:06:22 Log started: 2019-09-13 06:06:23 Preparing to unpack .../libexpat1_2.2.5-3ubuntu0.2_amd64.deb ... Unpacking libexpat1:amd64 (2.2.5-3ubuntu0.2) over (2.2.5-3ubuntu0.1) ... Setting up libexpat1:amd64 (2.2.5-3ubuntu0.2) ... Processing triggers for libc-bin (2.27-3ubuntu1) ... Log ended: 2019-09-13 06:06:25The pacakges show up with dpkg
# dpkg -l | grep "^r" rc linux-image-4.15.0-1037-aws 4.15.0-1037.39 amd64 Linux kernel image for version 4.15.0 on 64 bit x86 SMP rc linux-image-4.15.0-1039-aws 4.15.0-1039.41 amd64 Linux kernel image for version 4.15.0 on 64 bit x86 SMP rc linux-image-4.15.0-1047-aws 4.15.0-1047.49 amd64 Linux kernel image for version 4.15.0 on 64 bit x86 SMP rc linux-modules-4.15.0-1037-aws 4.15.0-1037.39 amd64 Linux kernel extra modules for version 4.15.0 on 64 bit x86 SMP rc linux-modules-4.15.0-1039-aws 4.15.0-1039.41 amd64 Linux kernel extra modules for version 4.15.0 on 64 bit x86 SMP rc linux-modules-4.15.0-1047-aws 4.15.0-1047.49 amd64 Linux kernel extra modules for version 4.15.0 on 64 bit x86 SMPFor me this looks like the original packages for the AWS installation. I left it as is.
root@ip-172-30-0-137-aws:~# apt update & apt dist-upgrade [1] 21857 Reading package lists... Done Hit:1 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic InRelease Get:2 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic-updates InRelease [88.7 kB] Get:3 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic-backports InRelease [74.6 kB] Get:4 http://security.ubuntu.com/ubuntu bionic-security InRelease [88.7 kB] Building dependency tree Reading state information... Done Calculating upgrade... Done The following packages were automatically installed and are no longer required: linux-aws-headers-4.15.0-1056 linux-aws-headers-4.15.0-1057 linux-aws-headers-4.15.0-1058 linux-aws-headers-4.15.0-1060 linux-aws-headers-4.15.0-1063 Use 'apt autoremove' to remove them. 0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded. Fetched 252 kB in 1s (267 kB/s) Reading package lists... Done Building dependency tree Reading state information... Done All packages are up to date. [1]+ Done apt update root@ip-172-30-0-137-aws:~#
root@ip-172-30-0-137-aws:~/upgrade20.04# apt install update-manager-core Reading package lists... Done Building dependency tree Reading state information... Done update-manager-core is already the newest version (1:18.04.11.12).
root@ip-172-30-0-137-aws:~/upgrade20.04# df -h Filesystem Size Used Avail Use% Mounted on udev 971M 0 971M 0% /dev tmpfs 199M 820K 198M 1% /run /dev/xvda1 24G 15G 8.5G 64% / tmpfs 993M 0 993M 0% /dev/shm tmpfs 5.0M 0 5.0M 0% /run/lock tmpfs 993M 0 993M 0% /sys/fs/cgroup /dev/loop0 94M 94M 0 100% /snap/core/9066 /dev/loop1 18M 18M 0 100% /snap/amazon-ssm-agent/1566 /dev/loop2 94M 94M 0 100% /snap/core/8935 /dev/loop3 18M 18M 0 100% /snap/amazon-ssm-agent/1480 /dev/xvdf1 73G 40G 30G 58% /home tmpfs 199M 0 199M 0% /run/user/1001 root@ip-172-30-0-137-aws:~/upgrade20.04#
root@ip-172-30-0-137-aws:~/upgrade20.04# do-release-upgrade Checking for a new Ubuntu release There is no development version of an LTS available. To upgrade to the latest non-LTS develoment release set Prompt=normal in /etc/update-manager/release-upgrades. root@ip-172-30-0-137-aws:~/upgrade20.04#
root@ip-172-30-0-137-aws:~/upgrade20.04# cat /etc/update-manager/release-upgrades # Default behavior for the release upgrader. [DEFAULT] # Default prompting behavior, valid options: # # never - Never check for, or allow upgrading to, a new release. # normal - Check to see if a new release is available. If more than one new # release is found, the release upgrader will attempt to upgrade to # the supported release that immediately succeeds the # currently-running release. # lts - Check to see if a new LTS release is available. The upgrader # will attempt to upgrade to the first LTS release available after # the currently-running one. Note that if this option is used and # the currently-running release is not itself an LTS release the # upgrader will assume prompt was meant to be normal. Prompt=lts
root@ip-172-30-0-137-aws:~/upgrade20.04# do-release-upgrade -d
new try:
root@ip-172-30-0-137-aws:~/upgrade20.04# grep -i clientaliveinterval /etc/ssh/sshd_config #ClientAliveInterval 0 ClientAliveInterval 60
root@ip-172-30-0-137-aws:~/upgrade20.04# grep -i prompt /etc/update-manager/release-upgrades # Default prompting behavior, valid options: # upgrader will assume prompt was meant to be normal. Prompt=lts #Prompt=normal
do-release-upgrade -d
Reading cache Checking package manager Continue running under SSH? This session appears to be running under ssh. It is not recommended to perform a upgrade over ssh currently because in case of failure it is harder to recover. If you continue, an additional ssh daemon will be started at port '1022'. Do you want to continue? Continue [yN] y Starting additional sshd To make recovery in case of failure easier, an additional sshd will be started on port '1022'. If anything goes wrong with the running ssh you can still connect to the additional one. If you run a firewall, you may need to temporarily open this port. As this is potentially dangerous it's not done automatically. You can open the port with e.g.: 'iptables -I INPUT -p tcp --dport 1022 -j ACCEPT' To continue please press [ENTER]
A new firewall rule has been added to the neweraws security group on AWS console. It allows
my home ip to aws:1022 (and probably to neweraws:1022)
tested before continue.
Reading package lists... Done Building dependency tree Reading state information... Done Hit http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic InRelease Get:1 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic-updates InRelease [88.7 kB] Get:2 http://eu-west-1.ec2.archive.ubuntu.com/ubuntu bionic-backports InRelease [74.6 kB] Get:3 http://security.ubuntu.com/ubuntu bionic-security InRelease [88.7 kB] Fetched 252 kB in 0s (0 B/s)
.....
.....
No candidate ver: linux-modules-4.15.0-1063-aws Do you want to start the upgrade? 17 installed packages are no longer supported by Canonical. You can still get support from the community. 7 packages are going to be removed. 162 new packages are going to be installed. 579 packages are going to be upgraded. You have to download a total of 276 M. This download will take about 1 minute with your connection. Installing the upgrade can take several hours. Once the download has finished, the process cannot be canceled. Continue [yN] Details [d]
d gives:
No longer supported: gcc-8-base geoip-database libargon2-0 libdumbnet1 libgeoip1 libiptc0 liblxc-common liblxc1 libncurses5 libncursesw5 libtinfo5 lxcfs lxd lxd-client python3-asn1crypto uidmap xdelta3 Remove: libapt-inst2.0 libapt-pkg5.0 libpolkit-backend-1-0 Remove (was auto installed) libmailutils5 libpython-stdlib python python-minimal Install: alsa-topology-conf alsa-ucm-conf bind9-dnsutils bind9-libs bind9-utils bolt cpp-9 cryptsetup-initramfs cryptsetup-run dbus-user-session dconf-gsettings-backend dconf-service finalrd fwupd fwupd-signed gcc-10-base gcc-9 gcc-9-base gir1.2-packagekitglib-1.0 glib-networking glib-networking-common glib-networking-services gsettings-desktop-schemas guile-2.2-libs kpartx libaio1 libappstream4 libapt-pkg6.0 libarchive13 libargon2-1 libasan5 libasound2 libasound2-data libbrotli1 libcanberra0 libcbor0.6 libcommon-sense-perl libcrypt-dev libcrypt-openssl-random-perl libcrypt1 libctf-nobfd0 libctf0 libdconf1 libdigest-bubblebabble-perl libdns-export1109 libefiboot1 libefivar1 libevent-2.1-7 libffi7 libfido2-1 libfl2 libfwupd2 libfwupdplugin1 libgcab-1.0-0 libgcc-9-dev libgcc-s1 libgdbm6 libglib2.0-bin libgpg-error-l10n libgpgme11 libgstreamer1.0-0 libgudev-1.0-0 libgusb2 libhogweed5 libicu66 libip4tc2 libip6tc2 libisc-export1105 libisl22 libjansson4 libjson-c4 libjson-glib-1.0-0 libjson-glib-1.0-common libjson-perl libjson-xs-perl liblmdb0 liblua5.3-0 liblvm2cmd2.03 libmail-authenticationresults-perl libmailutils6 libmaxminddb0 libmysqlclient21 libncurses6 libncursesw6 libnet-dns-sec-perl libnetplan0 libnettle7 libnftnl11 libntfs-3g883 libogg0 libpackagekit-glib2-18 libpcre2-8-0 libperl4-corelibs-perl libperl5.30 libplymouth5 libprocps8 libproxy1v5 libpython2-stdlib libpython3.8 libpython3.8-minimal libpython3.8-stdlib libreadline8 libsgutils2-2 libsmbios-c2 libsodium23 libsoup2.4-1 libssh-4 libstemmer0d libtdb1 libtinfo6 libtss2-esys0 libtypes-serialiser-perl libubsan1 libuchardet0 liburcu6 libvorbis0a libvorbisfile3 libxmlb1 linux-aws-headers-5.4.0-1009
Y starts the upgrade
I did select yes for restart services during the upgrade
some output about amavis need to be checked !!!!!
.....dpkg: warning: package not in status nor available database at line 53: linux-headers-4.15.0-1032-aws:amd64
dpkg: warning: package not in status nor available database at line 54: linux-aws-headers-4.15.0-1032:all
dpkg: warning: package not in status nor available database at line 55: linux-headers-4.15.0-1065-aws:amd64
dpkg: warning: package not in status nor available database at line 56: linux-aws-headers-4.15.0-1065:all
dpkg: warning: package not in status nor available database at line 61: multiarch-support:amd64
dpkg: warning: package not in status nor available database at line 63: perl-modules-5.26:all
dpkg: warning: package not in status nor available database at line 64: python-certbot-apache:all
dpkg: warning: found unknown packages; this might mean the available database
is outdated, and needs to be updated through a frontend method;
please see the FAQ <https://wiki.debian.org/Teams/Dpkg/FAQ>
(Reading database ... 72694 files and directories currently installed.)
Purging configuration files for linux-modules-4.15.0-1065-aws (4.15.0-1065.69) ...
dpkg: warning: while removing linux-modules-4.15.0-1065-aws, directory '/lib/modules/4.15.0-1065-aws' not empty so not removed
Purging configuration files for linux-image-4.15.0-1032-aws (4.15.0-1032.34) ...
Purging configuration files for libssl1.0.0:amd64 (1.0.2n-1ubuntu5.3) ...
Purging configuration files for ureadahead (0.100.0-21) ...
Purging configuration files for libpython3.6-minimal:amd64 (3.6.9-1~18.04ubuntu1) ...
Purging configuration files for python3.6-minimal (3.6.9-1~18.04ubuntu1) ...
Purging configuration files for linux-modules-4.15.0-1032-aws (4.15.0-1032.34) ...
Purging configuration files for linux-image-4.15.0-1065-aws (4.15.0-1065.69) ...
System upgrade is complete.
Restart required
To finish the upgrade, a restart is required.
If you select 'y' the system will be restarted.
Continue [yN]
Na reboot
jean@ip-172-30-0-137-aws:~$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 20.04 LTS
Release: 20.04
Codename: focal
1) After reboot named got problems because our bind9 needs access to /etc/bind/extern.slave
root@ip-172-30-0-137-aws:/etc/apparmor# grep extern /etc/apparmor.d/usr.sbin.named # we store secondaries in /etc/bind/extern.slave /etc/bind/extern.slave/** rw,
After systemctl restart apparmor ; systemctl restart bind9
Named works as expected.
2) /etc/ssh/sshd_config.d/aws.conf gemaakt, voorlopig nog
niet strikt genooeg !
root@ip-172-30-0-137-aws:/etc/ssh# cat /etc/ssh/sshd_config.d/aws.conf # config for aws.huens.be # default we disbale ssh authentication with clear text passwords # but during upgrade this is allwed #PasswordAuthentication no PasswordAuthentication yes #UseLogin no # for sofware upgrade from ubuntu 18-04 to 20-04 ClientAliveInterval 60
3) Dovecot
I di dtry to make a backup of the config files when the install script warned about them, but
i copied the new files>
therefore I had to recreate
/etc/dovecot/
root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# diff 10-mail.conf 10-mail.conf.20-04 30,31c30 < #mail_location = mbox:~/mail:INBOX=/var/mail/%u < mail_location = maildir:~/Maildir --- > mail_location = mbox:~/mail:INBOX=/var/mail/%u
root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# diff 10-ssl.conf 10-ssl.conf.20-04 12,15c12,13 < #ssl_cert = </etc/dovecot/private/dovecot.pem < #ssl_key = </etc/dovecot/private/dovecot.key < ssl_cert = </etc/letsencrypt/live/www2.huens.be/fullchain.pem < ssl_key = </etc/letsencrypt/live/www2.huens.be/privkey.pem --- > ssl_cert = </etc/dovecot/private/dovecot.pem > ssl_key = </etc/dovecot/private/dovecot.key root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# grep auth_mechanisms 10-auth.conf auth_mechanisms = plain login
root@ip-172-30-0-137-aws:/etc/dovecot/conf.d# diff 10-master.conf 10-master.conf.20-04 100,104c100,104 < ## unix_listener auth-userdb { < ## #mode = 0666 < ## #user = < ## #group = < ## } --- > unix_listener auth-userdb { > #mode = 0666 > #user = > #group = > } 110,115d109 < unix_listener /var/spool/postfix/private/auth { < mode = 0660 < # Assuming the default Postfix user and group < user = postfix < group = postfix < }
A long time after the upgrade I did detect that
/etc/apt/sources.list did contain bionic instead of focal (20.04 is focal ...)
Changed by hand to focal and the apt update; apt dist-upgrade.
repeated on 20200726 with bionic-security to focal-security (no effect seen.)