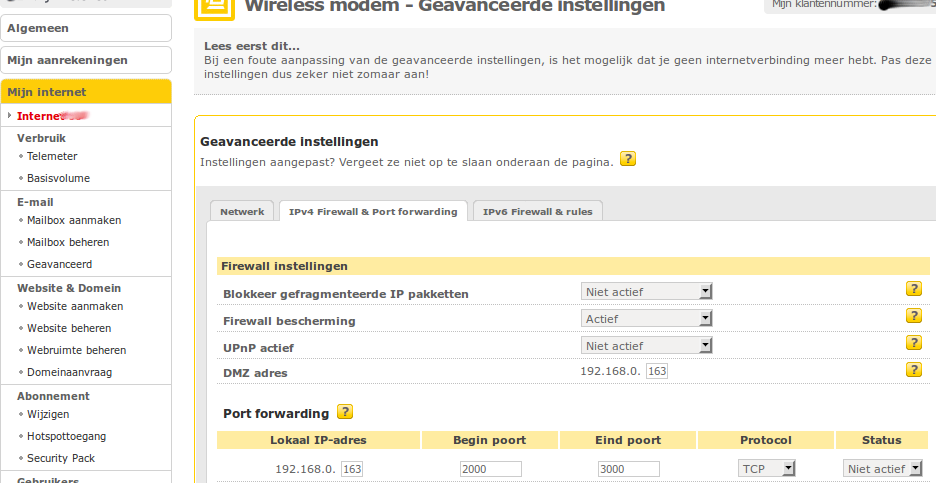
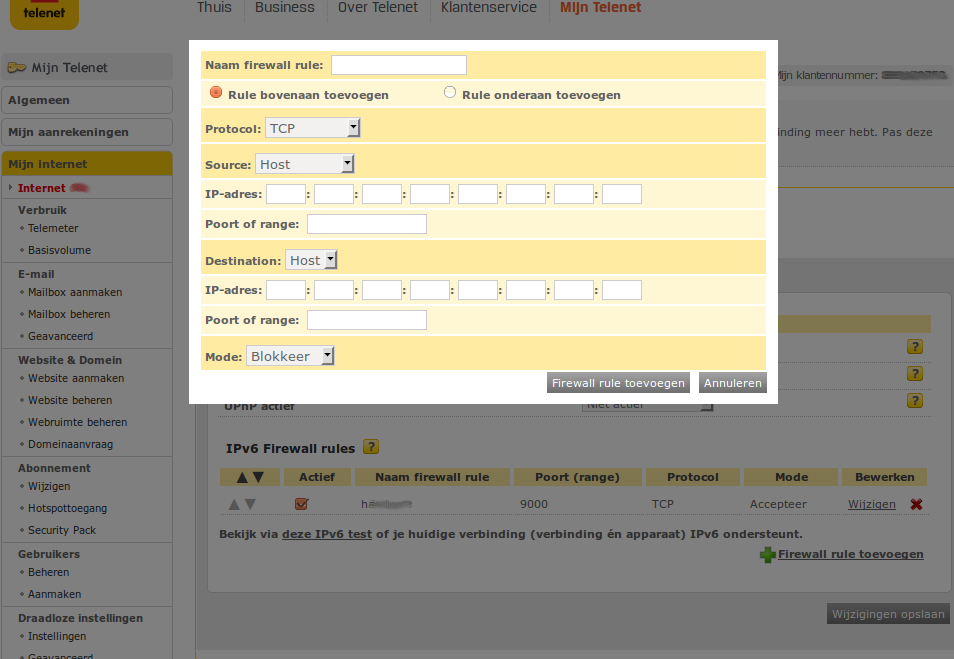
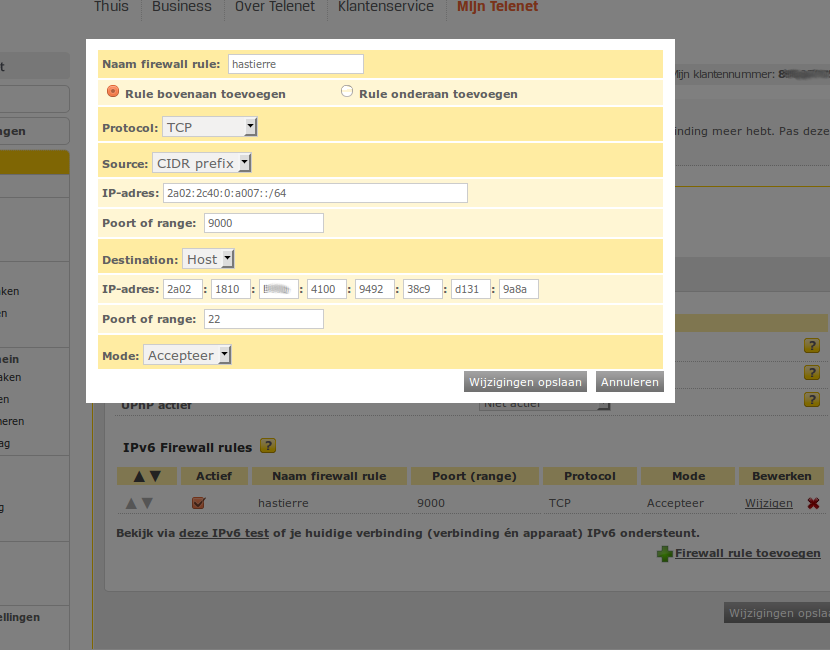
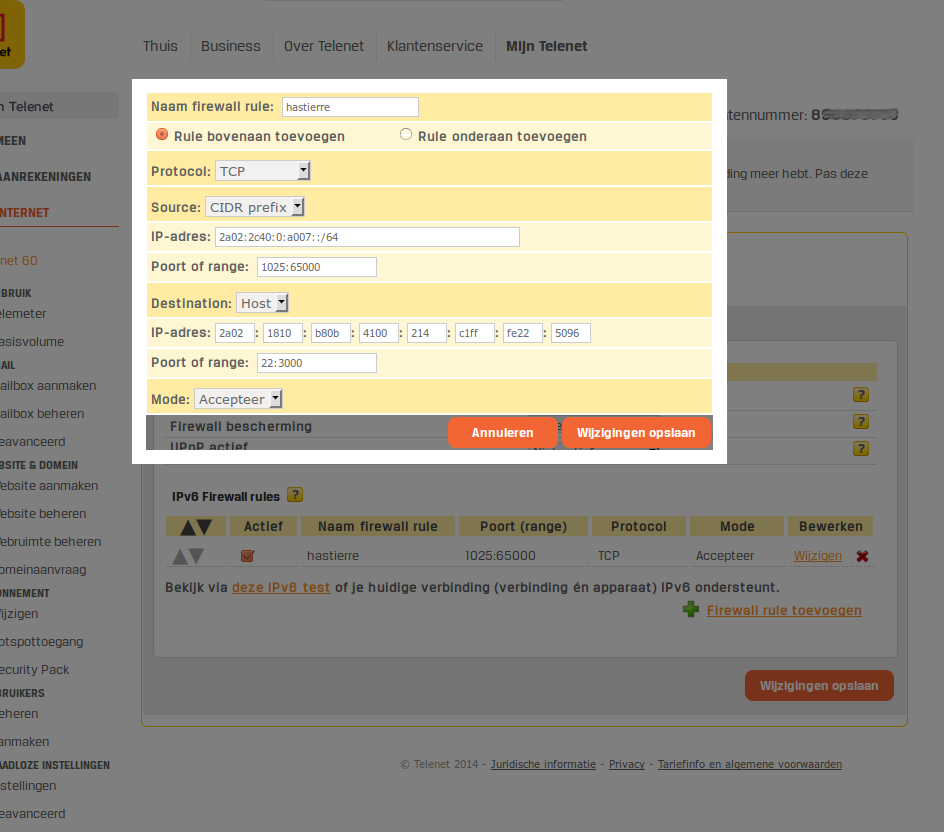
The destination address is the global dynamic adress of my home ssh server. Found under Linux with :
hastierre:~$ ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
...
4: ...0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:14:c1:22:50:96 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.163/24 brd 192.168.0.255 scope global wlan0
inet6 2a02:1810:b80b:4100:51ad:2483:6a14:ea88/64 scope global temporary dynamic
valid_lft 566766sec preferred_lft 48366sec
inet6 2a02:1810:b80b:4100:214:c1ff:fe22:5096/64 scope global dynamic
valid_lft 566766sec preferred_lft 48366sec
inet6 fe80::214:c1ff:fe22:5096/64 scope link
valid_lft forever preferred_lft forever